Here is an interesting statistic: nearly 33 percent of security breaches go undetected for months simply because organizations lack proper audit logs and cannot respond in real-time. It reveals a dangerous cybersecurity gap.
It is not always the hackers’ advanced tactics that cause the unthinkable damage. Often, it is the lack of visibility into credential activity that leaves businesses clueless. It raises a critical question: how can teams be assured that their passwords are not only stored securely but also tracked for every action taken?
The answer lies in audit trails, a feature that has become non-negotiable in modern password management.
Confused about what it is and how it is beneficial to you? Continue reading.
➡️This blog is designed for enterprises, startups, teams, and individual firms looking to strengthen credential security and improve oversight.
You will learn why audit logs matter, how they work, and how All Pass Hub makes them both secure and effortless. By the end, you will see how a password manager with audit logs helps prevent financial loss, reputation damage, and unnecessary stress.
Get ready to uncover how audit trails are the missing piece of puzzle in password security and how All Pass Hub turns them into a competitive advantage.
What Are Audit Logs In Password Managers?
Imagine giving several employees access to sensitive credentials without knowing who logged in, when changes happened, or whether anything suspicious took place. That kind of blind spot can cost businesses not only money but also their credibility. It is where audit logs step in.
At its simplest, an audit log in password management is a chronological record of every vital activity. It tracks actions such as password creation, sharing, editing, deletion, and failed login attempts.
Beyond that, it captures crucial details such as who acted, the exact time, the device used, and even the location.
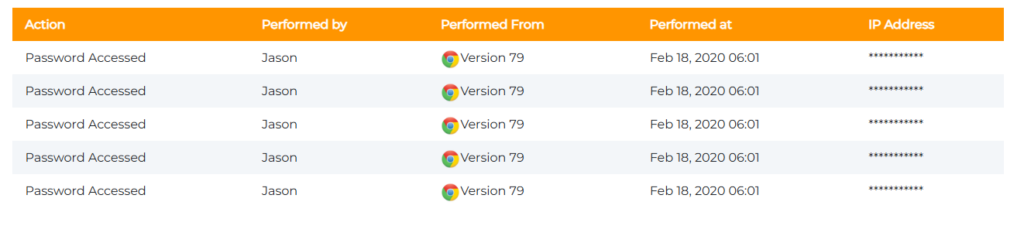
Think of it as a security camera for your digital vault, recording every movement so nothing goes unnoticed under your nose. Unlike basic activity reports, audit trails are built for security and compliance, ensuring actions are both transparent and tamper-proof.
➡️In password managers, these logs are not just helpful; they are integral. Without them, teams lose the ability to detect threats early, enforce compliance, and hold users accountable for unethical practices.
The Crux: Audit logs in password managers act like a security camera for your credentials. They record every activity with time, user, and context, ensuring complete visibility and accountability.
How Do Password Manager Audit Logs Work?
Audit logs are more than background records. They operate as your silent watchdog, ensuring that no action within your password manager goes ignored. Understanding how they work helps you see why they are integral for both security and compliance.
Here’s what happens behind the scenes:
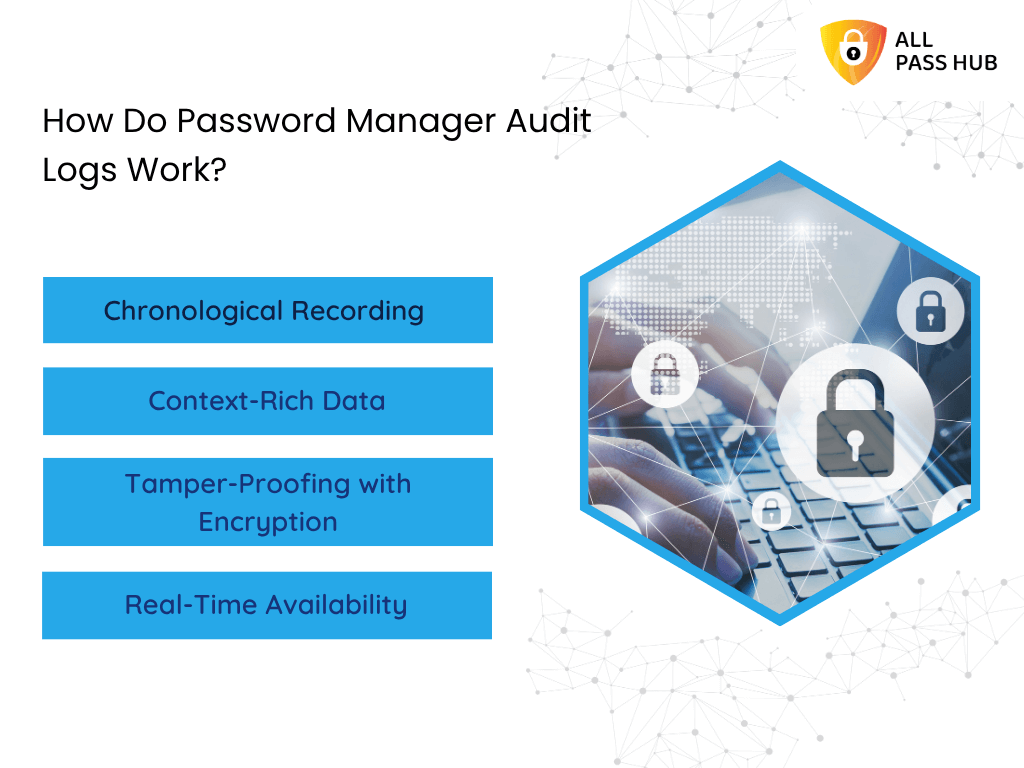
- Chronological Recording: Every event is logged in the order it occurs, from password creation and edits to credential sharing, deletions, and failed login attempts.
- Context-Rich Data: Each entry includes details such as the username, exact time, device, and even location. It creates a comprehensive picture of every action.
- Tamper-Proofing with Encryption: Logs are protected through secure encryption so they cannot be altered or deleted by malicious actors.
- Real-Time Availability: Audit trails are not just stored data; they are live records that can be retrieved instantly for monitoring or investigations.
Together, these elements provide transparency and control. Without them, you are left with unseen areas that cybercriminals and insider threats are quick to exploit.
Main Point: Password manager audit logs work by recording every action chronologically. It enriches each entry with user and device context, and guards logs with encryption for real-time visibility and protection.
Why Audit Logs Are Essential For Password Security
Cybersecurity is no longer just about keeping outsiders away. Many threats come from within teams, or slip in quietly through unacknowledged weak spots. Without audit logs, you may never know who accessed sensitive credentials. You will also be unaware whether a failed login attempt was harmless or hostile, or how long a risk has been hiding.
Here’s why audit logs are the compass to supervise all directions:
- Detect Unauthorized Access: If someone attempts to enter vaults without permission, logs provide the first red flag before severe damage happens.
- Spot Brute Force Attempts: Repeated failed logins or suspicious access patterns can signal cyberattacks in progress.
- Uncover Insider Misuse: Audit logs track credential sharing, ensuring no one exploits their role for harmful activities.
- Ensure Accountability: Every action is tied to a user and timestamp, making it transparent who is responsible for each change.
Without audit trails, password managers become vulnerable points that attackers can exploit, and the regulators will flag them. With them, you obtain the confidence of visibility, control, and compliance.
Must-Know Insight: Audit logs are vital for password security because they pinpoint threats, reveal suspicious patterns, ensure accountability, and provide early warnings before breaches escalate into disasters.
Key Components Of A Secure Audit Trail
An audit trail is only as good as the details it captures. Think of it as a detective’s notebook, where every clue must be written clearly, preserved safely, and easy to recall when needed. The notebook turns into an unreadable mess without the right components.
Here are the essentials every secure audit log must have:
- Time-Stamped Records: Every login, password change, or deletion must be marked with a precise date and time. It provides teams with a crystal-clear timeline to investigate suspicious events and confirm legitimate actions.
- User and Role Tracking: Logs should link each action to a person and their role. It prevents finger-pointing and creates accountability across the board.
- IP Address Visibility: Capturing the IP address of every login adds a vital layer of clarity, helping you track down unusual access from foreign locations or unrecognized devices.
- Session History and Activity Search: Investigations should not feel like hunting for a needle in a haystack. Quick search functions enable you to pull up specific details in seconds, saving valuable time during uncertainty.
- Tamper-Proof Storage with Encryption: Logs should be stored in a way that prevents unauthorized edits. Encrypted, tamper-proof storage ensures evidence remains intact for audits or investigations.
- Easy Export and Reporting: Secure audit trails must also be practical. The ability to export logs for compliance, forensic review, or simple backup ensures accessibility without complexity.
- Real-Time Monitoring and Alerts: The best logs do more than store history. They actively alert you when unusual activity occurs, allowing immediate response before risks spiral out of control.
These components transform audit logs from a dry technical requirement into a living shield, one that detects, documents, and defends suspicious movement.
➡️Guess what? All these elements are available for less than the cost of a cup of coffee with the All Pass Hub Premium plan. It starts at just $0.99/month and $6.99/year.
Not only that, there are handy features beyond audit logs and import/export history. Isn’t that a flavor explosion and magical beat at an economical price?
Smart Summary: A secure audit trail combines precise time stamps, user accountability, IP tracking, tamper-proof storage, and real-time login monitoring. All this ensures nothing slips past undiscovered in your password manager.
Read More:- What Makes All Pass Hub The Ideal Password Manager For Teams
Best Practices For Audit Logging In Password Managers
An audit trail is powerful only when it is managed wisely. Many businesses create logs but fail to maintain them properly, turning valuable data into clutter that is never reviewed. By following best practices, you can turn your logs into a strategic asset that strengthens both security and compliance.
Here’s how to make audit logging work for you:
- Define What Matters Most: Not every event needs to be documented. Focus on high-value activities such as logins, vault access, password changes, credential sharing, and failed login attempts.
- Secure Log Storage with Encryption: Logs are often the first target in a breach. Storing them with encryption ensures attackers cannot tamper with or erase critical evidence.
- Centralize Logs for Visibility: Spread-out data makes investigations a nightmare. A centralized system, ideally integrated with Security Information and Event Management (SIEM) tools, ensures you see the whole story without vulnerable points.
- Review Logs Regularly: Audit trails aren’t about collecting dust. Schedule periodic reviews to locate suspicious activity, compliance gaps, or repeated weak practices.
- Automate Alerts and Reporting: Manual tracking is slow and prone to errors. Automated alerts for failed logins, unusual access, or mass credential changes keep you one step ahead of attackers.
- Use Dashboards for Quick Insights: A well-designed dashboard transforms endless entries into digestible insights. It saves time and helps IT teams respond rapidly.
By implementing these practices, you avoid the trap of “logs in name only.” Instead, you create an intelligent, always-ready system that not only records history but actively prevents crises.
Knowledge Drop: Audit logging becomes meaningful when events are prioritized, logs are encrypted and centralized, reviews are regular, and alerts are automated. All this ensures proactive defense rather than reactive cleanup.
Common Challenges Without Audit Trails
Imagine driving at night with no headlights. That is what managing passwords without audit trails feels like. You might move forward, but every mile traveled increases the chance of a collision.
The absence of audit logs creates unmonitored points that criminals, careless insiders, and compliance auditors all can exploit.
Here are the most pressing challenges organizations face when audit logs are missing:
- Blind Spots in User Activity: Without records, you cannot hunt down who accessed credentials, when changes occurred, or whether unauthorized sharing took place.
- Insider Threats go Undetected: A dissatisfied or frustrated employee can misuse access and escape unseen, leaving no trail for investigation.
- Compliance Audit Failures: Regulators expect detailed activity records. Without them, organizations face fines, reputational damage, and failed certifications.
- Wasted IT Resources: Investigating incidents without data is like putting together a jigsaw puzzle with missing bits & pieces. IT teams spend countless hours chasing guesses instead of working with facts.
When audit trails are unaccounted for, every login becomes a risk, every password change a mystery, and every compliance audit a gamble.
Essential Insight: Without audit trails, organizations face voids, insider threats, failed compliance checks, and wasted IT resources. It leaves them vulnerable to both cyber risks and regulatory penalties.
Real-Time Monitoring & Anomaly Detection With Audit Logs
In today’s world, cyber threats do not politely knock. They strike suddenly, often using automated tools and AI-powered tactics to overwhelm defenses. Static logs alone are not sufficient. What organizations need is a shield that not only records history but also raises the alarm the moment danger bursts.
This is where real-time monitoring and anomaly detection steps in. They elevate audit trails from passive records to proactive guardians.
Here is how they help:
- Failed Login Patterns: Repeated unsuccessful attempts may point to brute force attacks. Real-time alerts highlight these red flags instantly.
- Privilege Escalation Attempts: When users suddenly try to access areas beyond their role, anomaly detection flags the suspicious behavior before it turns into a crisis.
- Unusual Sharing Activity: Logs can detect mass sharing of sensitive credentials, preventing insider misuse or account compromise.
- AI-Driven Anomaly Detection: Advanced systems can analyze large volumes of data. They can find subtle deviations that human eyes wouldn’t discover.
By layering these capabilities into audit trails, organizations gain visibility and foresight. Instead of reacting after damage happens, they respond as risks unfold.
Key Takeaway: Real-time monitoring and anomaly detection transform audit trails into a proactive shield. You can catch brute force attempts, privilege abuse, and AI-driven threats before they spiral into full-scale breaches.
Read More:- Secure Password Manager For Teams
Compliance & Regulations In 2025
Compliance is no longer optional. In 2025, regulators worldwide are intensifying their focus on data protection, transparency, and accountability. Password managers without appropriate audit logging risk not only breaches but also lead to costly fines and certification failures.
Audit logs serve as proof of diligence. They disclose to regulators that every action linked to password use is recorded, monitored, and guarded. For industries such as healthcare, finance, and legal services, these records are not just technical features; they are lifelines for compliance.
Here’s how audit trails map to key regulatory requirements:
| Regulation | Audit Log Expectations | How Audit Trails Help |
| GDPR | Accountability, access monitoring, data protection | Logs provide visibility into who accessed personal data, when, and why, supporting GDPR’s transparency principles. |
| HIPAA | Access logs for Protected Health Information (PHI) | Tracks every attempt to view or modify sensitive health data, ensuring HIPAA compliance in healthcare organizations. |
| SOC 2 | Security, availability, and processing integrity | Logs document all credential-related actions, demonstrating adherence to SOC 2 trust service principles. |
| PCI DSS | Monitoring access to payment systems | Logs create a traceable history of credential access, supporting PCI DSS requirements for payment card data. |
➡️For enterprises, the absence of audit trails means regulatory non-compliance, failed audits, and a tarnished reputation. However, with secure, tamper-proof logging, organizations gain both peace of mind and documented proof of compliance.
What You Should Know: Audit logs are critical for compliance in 2025. They provide verifiable records that adhere to GDPR, HIPAA, SOC 2, and PCI DSS requirements while protecting businesses from fines and reputational erosion.
Myths & Misconceptions About Audit Logs
Though audit logs are becoming standard in password management, several myths still cloud their value. Clearing these misconceptions is necessary so businesses and teams can embrace logs with confidence.
Here are common myths and misbeliefs that we are demystifying.
Myth 1: Audit Logs Are Only For Big Enterprises.
Reality: Small businesses face the same risks as large corporations, sometimes even more. Audit logs provide visibility into suspicious activity, helping smaller teams protect their credentials and meet compliance without extra complexity.
Myth 2: Logs Violate User Privacy.
Reality: Audit logs record actions, not personal content. They track events such as logins, changes, and sharing activities. It protects the organization while still respecting individual privacy.
Myth 3: Logs Are Too Expensive To Maintain.
Reality: Modern password managers, such as All Pass Hub, offer centralized, encrypted audit trails at scale without a fee per user. The price of ignoring logs is far higher, often measured in fines or breaches.
Myth 4: Logs Are Ineffective After A Breach.
Reality: Logs are the first source investigators turn to. They reveal what went wrong, who accessed sensitive data, and how the intrusion occurred. Without them, organizations remain in guesswork.
Core Insight: Audit logs are encircled by myths. However, the truth is they work for any business size, shield privacy, remain cost-effective, and are vital for compliance and breach investigations.
Cost vs. Benefit Of Audit Trails
Many organizations hesitate to implement audit logs because they perceive them as another expense. The reality is that the absence of audit trails can lead to substantial costs.
From compliance fines to wasted IT hours, the hidden price of not having them can be unimaginable. In contrast, audit logs deliver both measurable financial benefits and intangible reassurance.
Here’s how the costs stack against the benefits:
| Factor | Without Audit Trails | With Audit Trails |
| Compliance | Risk of fines, failed certifications, and reputational tarnish | Smooth audits, provable compliance with GDPR, HIPAA, SOC 2, PCI DSS |
| IT Resources | Countless hours investigating incidents manually | Streamlined investigations with centralized, searchable logs |
| Security | Vulnerable spots exploited by insider threats and hackers | Early detection of anomalies and unauthorized access attempts |
| Financial Impact | Potential losses from breaches and regulatory penalties | Reduced risk of costly breaches and improved ROI on security investments |
| Peace of Mind | Constant uncertainty and stress for admins and executives | Confidence knowing every action is tracked, encrypted, and tamper-proof |
The ROI of audit logs is not about dollars saved; it is in the assurance that your security backbone is future-ready and your compliance boxes are checked. All this empowers your leadership to focus on growth instead of damage control.
What This Means For You: Audit trails deliver significant ROI by reducing breach costs, saving IT resources, ensuring compliance, and providing peace of mind. All this outweighs the small investment of less than a dollar per month and $7 per year needed to maintain them.
Read More:- Why Do CTOs, Team Leads, And Administrators Love All Pass Hub
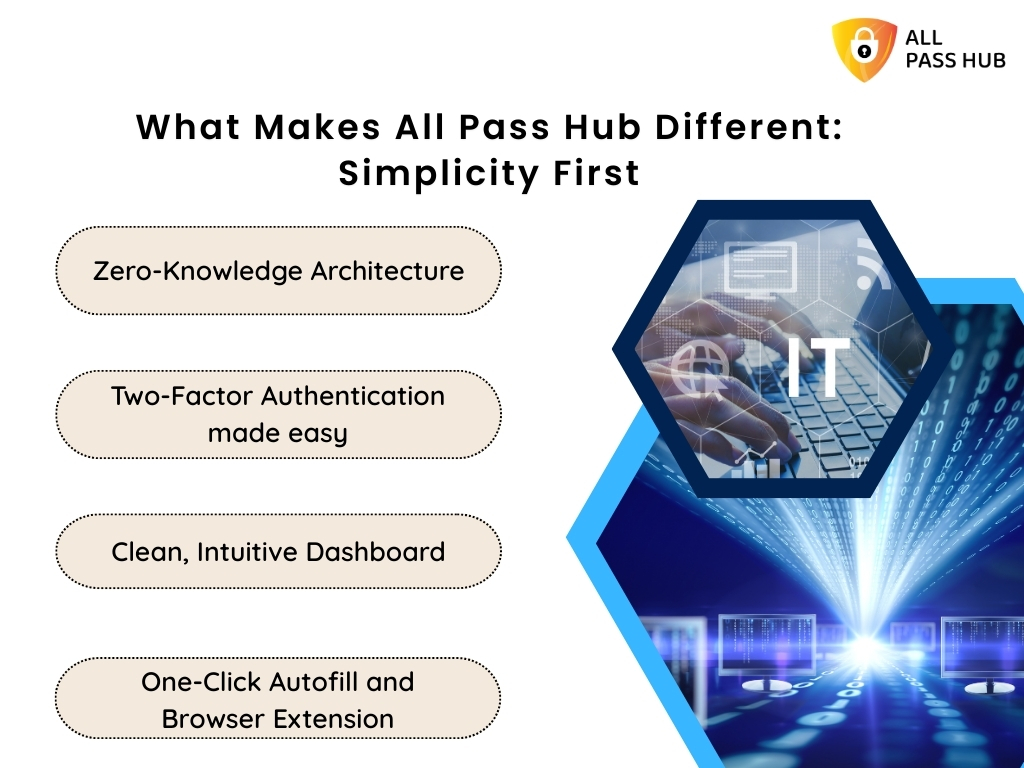
How All Pass Hub Delivers Transparent Audit Trails
Many password managers promise visibility. However, only a few make it both comprehensive and effortless. All Pass Hub aims to transform audit trails from a technical burden into a user-friendly safeguard that empowers both individuals and enterprises.
Here is how All Pass Hub delivers unmatched transparency:
- Centralized Activity Logs: All authentication data activity is tracked in one place, whether it is a login, password change, deletion, or credential share. With support for unlimited users, nothing goes unobserved through the cracks.
- Precise Time-Stamped Records: Every action is logged with an exact date and time, ensuring a reliable timeline for compliance and investigations.
- User and Role Accountability: Actions are linked to specific users and roles. It enables teams to view who did what and when.
- IP Address Tracking: Suspicious logins from unusual locations are quickly detected. It helps administrators act before damage escalates.
- Detailed Session History: Vault access and password updates are recorded in detail. It creates a holistic view of team activity.
- Quick Search and Filtering: No more endless scrolling. Administrators can instantly search logs to find precisely what they need. It saves time during audits or investigations.
- Easy Export for Compliance: Logs can be exported securely. It makes reporting simple during audits or when external stakeholders require proof of compliance.
- Tamper-Proof Storage with Encryption: Every log is protected through end-to-end encryption, ensuring data cannot be altered or deleted by unauthorized individuals.
By combining these features, All Pass Hub provides organizations with a transparent window into their password security posture without complexity or additional costs. It is a peace of mind security that feels practical, accessible, and growth-friendly.
In a Nutshell: All Pass Hub simplifies audit trails with centralized logs, time-stamped records, IP tracking, export options, and encrypted storage. All this equips teams with total visibility without adding complexity or hidden costs.
Real-World Use Cases
Audit logs are not just technical add-ons. They are lifelines in critical situations where visibility determines whether a business runs smoothly or spirals into chaos. Here are some practical scenarios where audit trails prove their worth.
Remote Teams Monitoring Credential Sharing
Imagine a distributed startup with employees logging in from different time zones.
- Without audit logs, leaders would have no way of knowing whether credentials are being shared responsibly.
- With centralized logs, every login, IP address, and activity is visible. It ensures remote collaboration is both productive and secure.
Enterprises Preparing For Compliance Audits
A financial firm is required to undergo a scheduled PCI DSS audit. Instead of crawling through spreadsheets or incomplete records, the compliance officer exports All Pass Hub’s detailed activity logs.
Every login and vault update is neatly documented, ticking off ✅ the auditor’s checklist 📋 in minutes rather than weeks.
Agencies Tracking Client Password Activity
A digital marketing agency manages dozens of client credentials. When a client asks who last accessed their account, the agency uses the password manager’s audit log to provide a precise time-stamped report.
It not only builds trust but also strengthens client relationships with transparency.
➡️Audit logs in these scenarios do more than record history. They create accountability, inspire confidence, and enable businesses to keep moving without fear of hidden risks.
Quick Recap: Real-world use cases prove that audit logs are crucial for remote collaboration, compliance readiness, and client trust. It turns transparency into a practical advantage for every organization.
Future Of Audit Trails In Password Management
The future of password security will not be decided by who has the strongest vault, but by who can detect and act on suspicious activity the fastest. As cyberattacks become more automated and sophisticated, audit trails are evolving from static records into intelligent systems that predict and prevent risks.
Here is what lies ahead:
- AI-driven Anomaly Detection: Artificial intelligence can scan vast amounts of log data in a fraction of a second. It can identify patterns such as coordinated login attempts or subtle insider misuse. Instead of relying only on human reviews, AI acts as a 24/7 guardian that never overlooks a clue.
- Forensic Logging for Investigations: Future audit trails will provide even deeper context, such as device fingerprints, geolocation analysis, and correlation across systems. This forensic-level detail helps teams reconstruct incidents with clarity, even months later.
- SIEM Integration for Centralized Defense: Security Information and Event Management (SIEM) platforms are becoming the hub of enterprise defense. When logs integrate seamlessly with SIEM, they provide a unified view of threats. It helps eliminate weak points across the entire security ecosystem.
- Log Analytics Dashboards: Interactive dashboards will turn endless entries into actionable intelligence. Instead of scrolling through raw data, teams can view trends, irregularities, and risk scores at a glance.
➡️Forward-thinking organizations will not wait until these features become optional add-ons. They will adopt platforms like All Pass Hub that already prepare for the future with a transparency-first design and future-ready audit logging.
Final Thought: The future of audit trails is defined by AI-driven detection, forensic insights, SIEM integration, and analytics dashboards. All of them turn logs into a predictive shield against tomorrow’s cybersecurity threats.
Conclusion
Password protection is no longer just about storing credentials securely. Businesses of all scales and sizes must prove accountability, fulfill strict compliance requirements, and stay ahead of ever-evolving cyber threats.
It is where audit trails shine. They provide profound visibility to every action, uncover suspicious behavior before it escalates, and create the transparency that regulators and clients now expect.
Throughout this blog, we explored what audit logs are, how they work, why they matter, and how they transform password security.
From real-time anomaly detection to compliance readiness, audit trails are more than records; they are a lifeline for enterprises, teams, and agencies navigating today’s high-stakes digital world.
All Pass Hub delivers these capabilities with precision. Its centralized activity logs, time-stamped records, IP tracking, easy export, and tamper-proof encryption ensure that organizations gain both security and peace of mind.
Whether you are a startup scaling quickly or an enterprise preparing for audits, All Pass Hub simplifies compliance and strengthens defenses without adding complexity.
➡️Opportunity is knocking on your door to grab the chance to move beyond guesswork and blind spots. Choose All Pass Hub, and step into a future where password management is transparent, secure, and ready for tomorrow’s challenges.
FAQ
How Do Audit Logs Improve Password Security?
Audit logs reinforce security by recording every action related to credentials, such as logins, edits, and sharing. This visibility helps detect unauthorized access, identify suspicious behavior, and hold users accountable for misconduct. It lowers the likelihood of hidden breaches.
Can Password Managers Track User Activity History?
Yes. Modern password managers track user activity by logging events with details such as time, user identity, IP address, and type of action performed. This activity history provides transparency, supports investigations, and ensures compliance with security regulations.
How To Enable Audit Logging In Password Managers?
Most enterprise-grade password managers enable audit logging automatically. In All Pass Hub, logs are centralized, encrypted, and available out of the box. Admins can review, filter, and export them without complex setup, making visibility straightforward and prompt.
What’s Included In Enterprise Audit Logs?
Enterprise audit logs include logins, failed attempts, password changes, sharing events, deletions, IP addresses, user roles, and timestamps. This comprehensive data set provides a detailed trail of activity for security monitoring, compliance reporting, and forensic investigations.
Are Audit Logs Required For Compliance Audits?
Yes. Standards such as GDPR, HIPAA, SOC 2, and PCI DSS expect verifiable audit trails. Logs provide the evidence regulators need, showing who accessed credentials, when, and why. It ensures accountability and avoids penalties during audits.
How Long Should Password Audit Logs Be Retained?
Retention depends on regulations and internal policies. For instance, HIPAA requires six years, while PCI DSS demands at least one year. Many enterprises preserve logs for between 12 and 24 months to meet compliance and support incident investigations.