What do lost spreadsheets, repeated password reset tickets, and frantic chat messages asking for login details have in common? They all point to a growing problem: chaotic password management.
In today’s digital workplace, teams rely on dozens of tools, from CRMs and HR platforms to cloud storage and project dashboards. However, without proper structure, login details end up scattered across chatting apps, sticky notes, and shared Excel files. It creates inefficiency and security risks.
That’s where a password manager for teams redefines everything. By centralizing access into encrypted vaults, setting role-based permissions, and enabling secure sharing, teams can collaborate with peace of mind.
From agencies and IT teams to HR and admin departments to remote groups and enterprises, every organization faces the same challenge. This blog is written for them.
It offers practical answers, proven benefits, and explains how features like role-based access and audit logs protect company data. You’ll discover how All Pass Hub empowers modern teams to work confidently, collaboratively, and securely.
So fasten your seatbelt to uncover a blueprint for protecting your business and transforming the way your team collaborates.
What Is A Team Password Manager?
In layperson terms, a team password manager is a secure, shared vault where organizations can store, manage, and distribute credentials without relying on spreadsheets or unsecured chat tools.
Unlike personal password managers, which are designed for individuals, team solutions are built for collaboration, supervision, and accountability.
Here’s how it works in practice:
- Centralized Password Management → Every login, key, and credential is stored in an encrypted repository accessible only to authorized team members.
- Role-Based Permissions → Admins, managers, and employees can be granted different levels of access. It ensures credentials are shared only with the authorized personnel.
- Encrypted Sharing → Instead of sending login details in emails, teams share access securely within the vault, eliminating leaks.
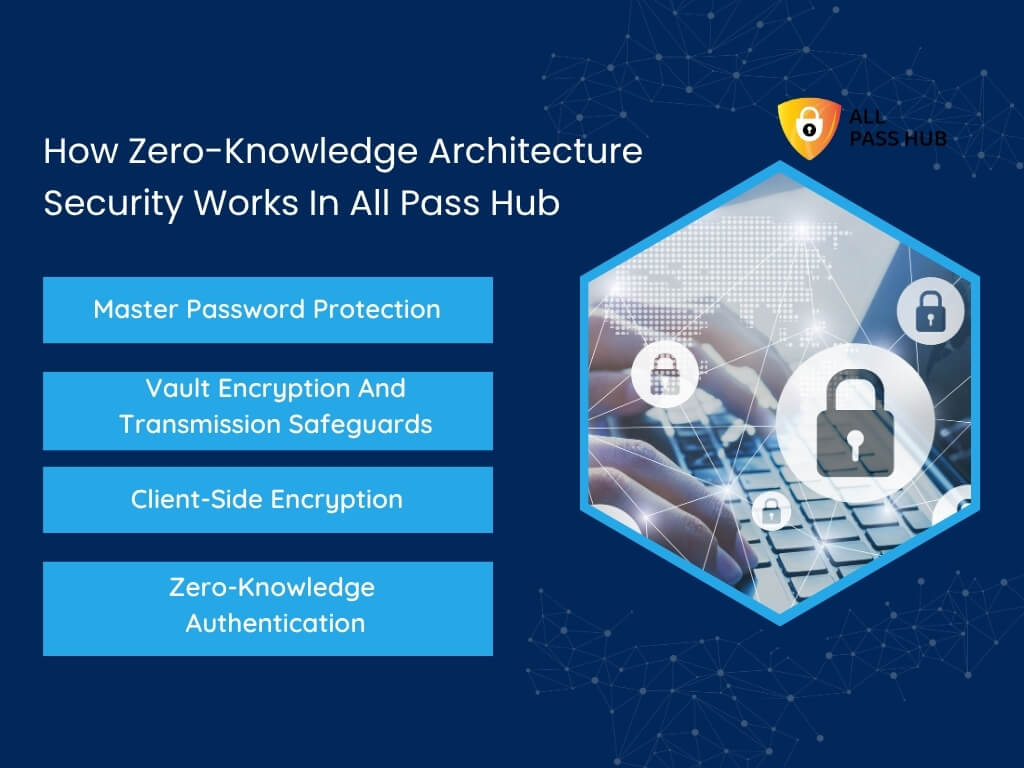
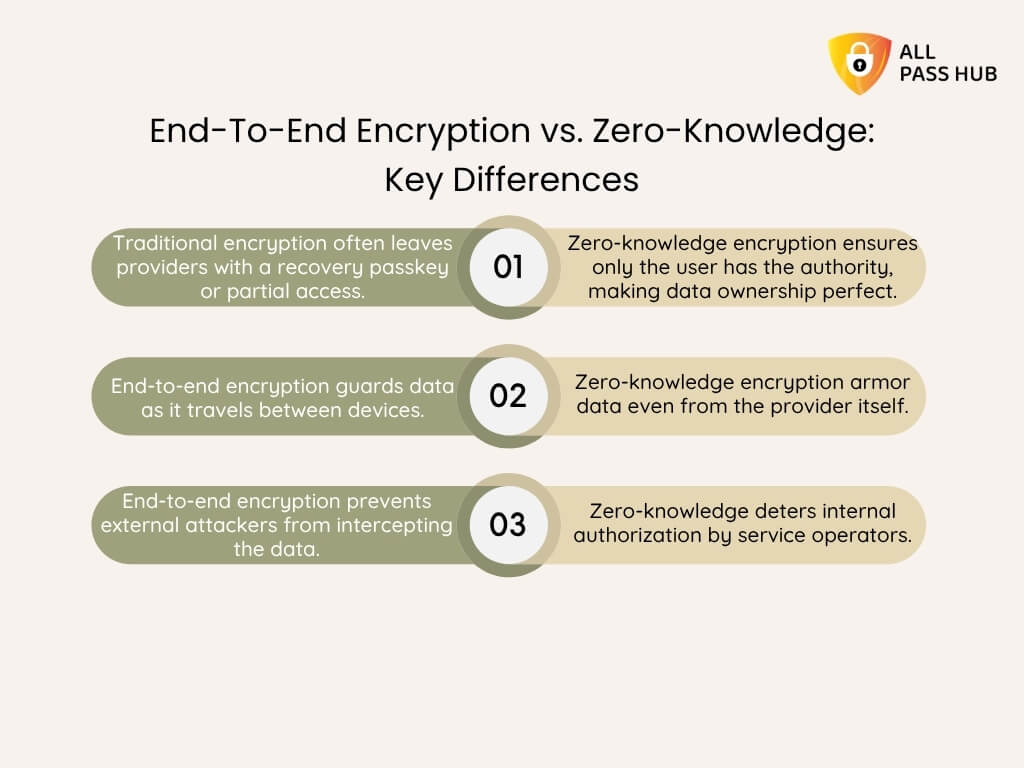
- Zero-Knowledge Design → The provider cannot view or decrypt the data, guaranteeing privacy and control remain with the business.
The significant shift here is cultural. Moving from scattered logins to a shared password manager for business means adopting a structure where credentials are not just protected but also easy to manage.
This balance of security and usability is why present-day teams are adopting zero-knowledge, collaborative password managers as a foundation of corporate password management.
The Crux: A team password manager centralizes credentials, adds oversight, and supports collaboration securely. It replaces outdated methods such as spreadsheets or informal sharing.
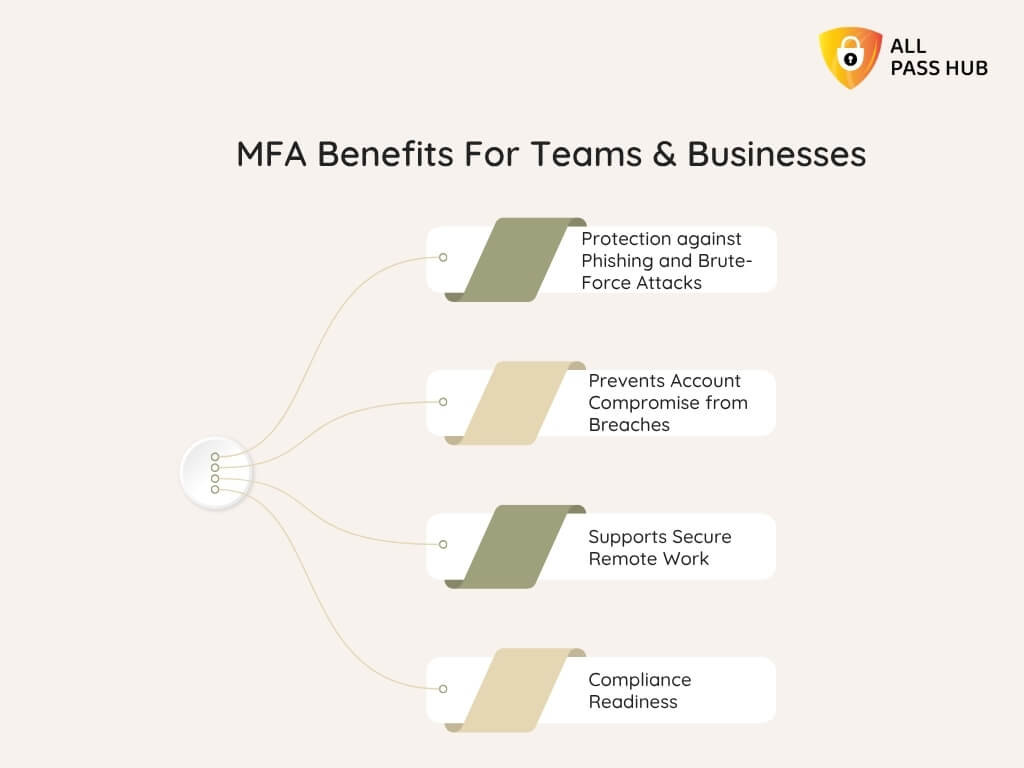
Why Do Teams Need Password Managers?
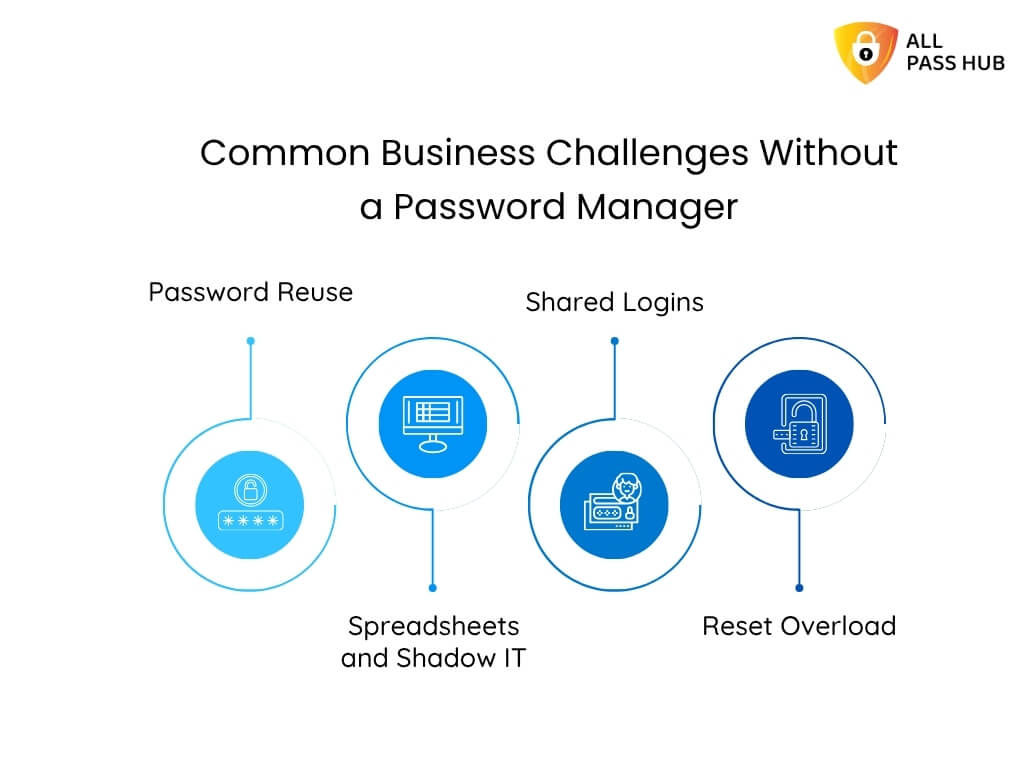
Every team, whether a five-person startup or a global agency, has numerous accounts. It includes CRMs, cloud drives, email suites, and project tools. Yet most still juggle passkeys through spreadsheets, sticky notes, or chat apps.
These shortcuts may feel convenient. However, they quietly open the door to security risks that cost businesses time, money, and credibility.
Here’s why teams can’t afford to depend on outdated practices:
- Password Reuse and Oversharing → When employees recycle the same credentials or share them casually, a single breach can compromise multiple systems.
- Spreadsheets as “Vaults” → Excel files or Google Sheets may organize logins, but they offer zero encryption, no access control, and no audit trail.
- Shadow IT Risks → Employees often create accounts outside of IT oversight, leaving credentials unmanaged and invisible until a breach occurs.
- Rising Reset Tickets → IT teams lose countless hours handling password resets, reducing productivity and frustrating both staff and management.
The cost is exorbitant. According to the IBM report, credential theft accounts for a large percentage of data breaches, often resulting in millions of dollars in damages.
Teams that fail to stop unsafe authentication data sharing or eliminate storage in spreadsheets are not only at risk of breaches but also face compliance penalties and reputational harm.
Core Insight: Team password managers replace scattered, insecure practices with structured, centralized control. It reduces the likelihood of credential theft, reduces reset tickets, and restores productivity.
The Lifecycle Of A Team Password: From Creation To Decommission
Think of a password like a key that moves through many hands in its lifetime. From the moment it is created until it is retired, that “pass key” can either protect the business or expose it to unnecessary risk. Understanding this journey helps teams see where weak points emerge and how a team password manager like All Pass Hub secures every step.
Here’s how a typical team login verification token travels through its lifecycle:
Creation
Passwords often begin life hurriedly, crafted to be easy to remember rather than resilient enough to resist attacks. Weak or recycled passwords are the foremost crack in the armor.
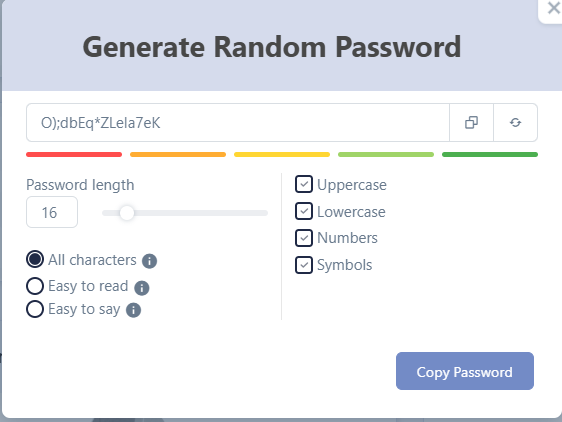
With All Pass Hub → A built-in password generator creates undecipherable, unique credentials by default, reducing human error from the beginning.
Storage
Authentication information often ends up in spreadsheets, notebooks, or chat threads without a systematic storage structure. One lost file can mean uncontrolled access.
With All Pass Hub → Every credential is stored inside an encrypted repository with zero-knowledge assurance. It ensures only authorized team members can use it.
Sharing
Teams share credentials daily, whether for social media logins or SaaS tools. Untracked sharing creates a trail that no one can trace back if something goes wrong.
With All Pass Hub → Secure sharing links and role-based permissions ensure credentials travel safely between teammates and are monitored with a transparent audit log.
Rotation
Accounts change roles, projects end, or vendors move on. Yet many access tokens never get rotated, leaving old passkeys swinging in the system.
With All Pass Hub → Password rotation is easy to enforce. Security dashboards and audit logs alert admins to outdated or risky credentials.
Revocation
When employees leave the organization or access is no longer needed, revoked passwords should close the door. Unfortunately, orphaned accounts are often forgotten.
With All Pass Hub → Admins can instantly revoke or reassign access, ensuring no digital doors stay open for former staff or third-party contractors.
The lifecycle of a password reveals one truth: security gaps appear not in one moment, but across every stage. All Pass Hub protects the entire journey, allowing teams to collaborate with confidence rather than chaos.
Main Message: By securing the comprehensive password lifecycle from creation to revocation, team password managers transform fragile, forgotten credentials into a controlled, auditable, and resilient system.
Here is something worth reading- Why Do CTOs, Team Leads, And Administrators Love All Pass Hub
Key Features That Matter (And Their Business Value)
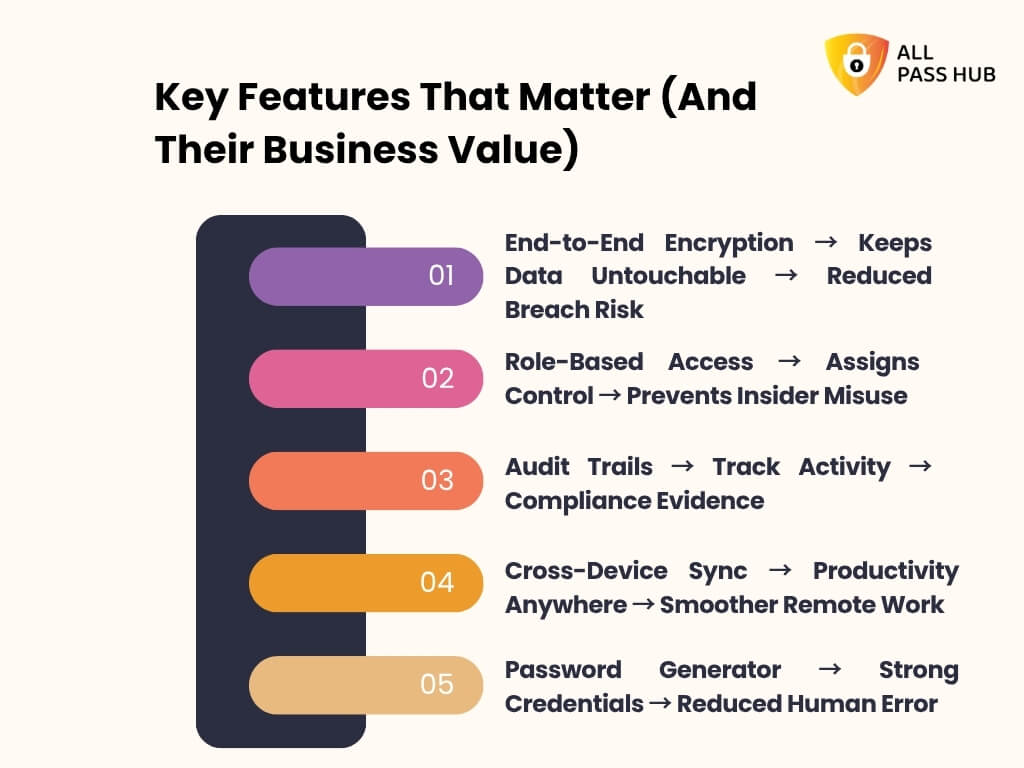
Features mean little if they don’t solve practical problems. A team password manager isn’t just a collection of security tools; it’s a way to eliminate daily hassle, lower risks, and cultivate trust across departments.
Let’s walk through the most critical features and the business value they deliver.
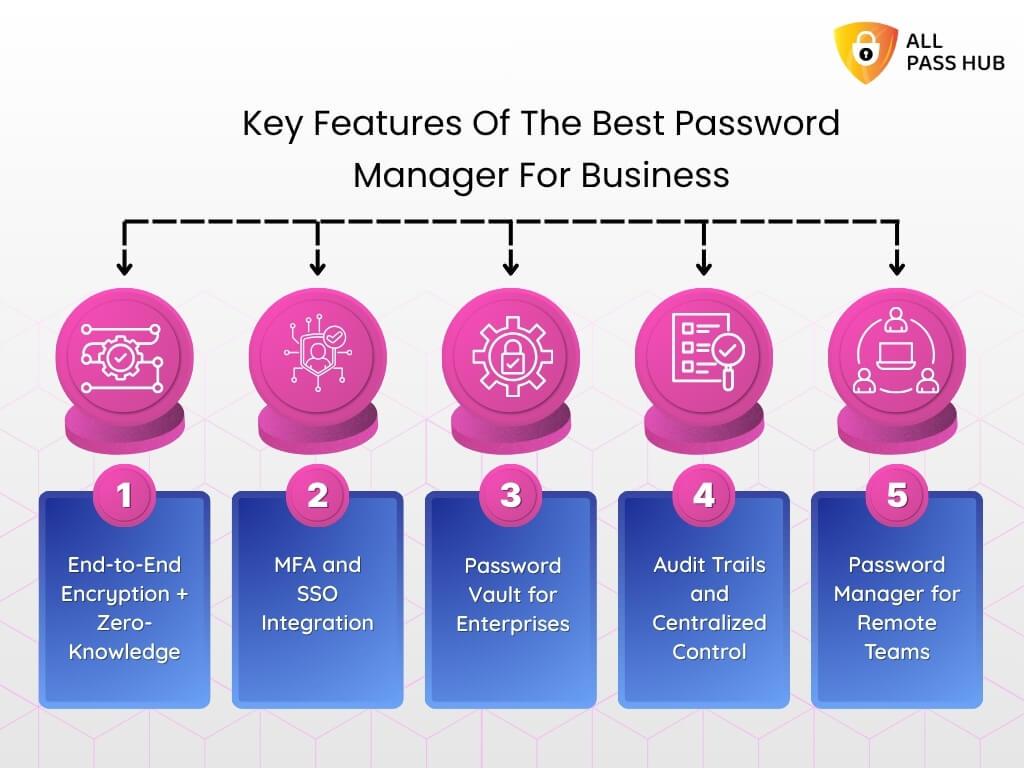
End-to-End Encryption → Keeps Data Untouchable → Reduced Breach Risk
Without encryption, stored credentials are like a diary left unlocked on a desk. End-to-end encryption with a zero-knowledge guarantee ensures that no one, not even the provider, can peep inside your vault.
- Business Value: Peace of mind that sensitive logins are safe from hackers, breaches, or accidental exposure.
Role-Based Access → Assigns Control → Prevents Insider Misuse
In many teams, “everyone knows the password” is a recipe for trouble. Role-based access provides admins with control of who views what.
- Business Value: Sensitive credentials stay in the right hands, reducing insider threats and maintaining accountability.
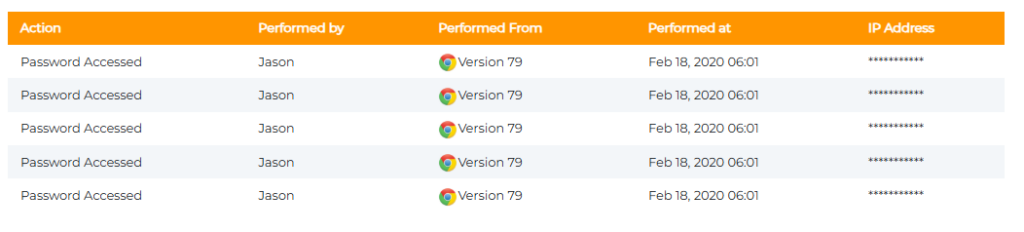
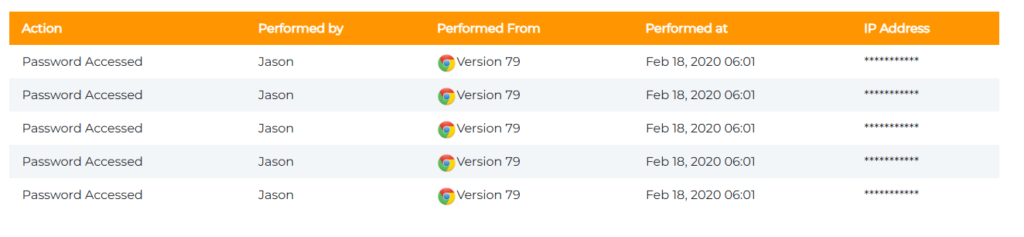
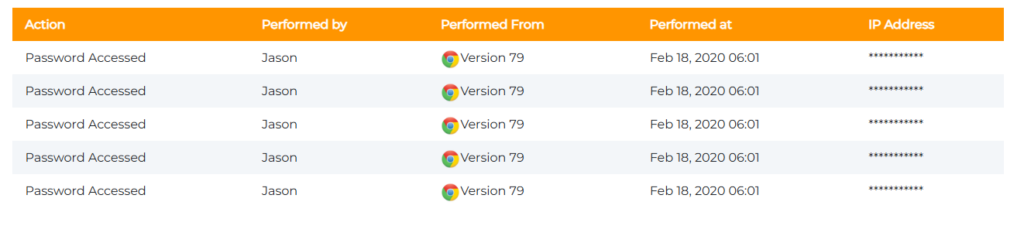
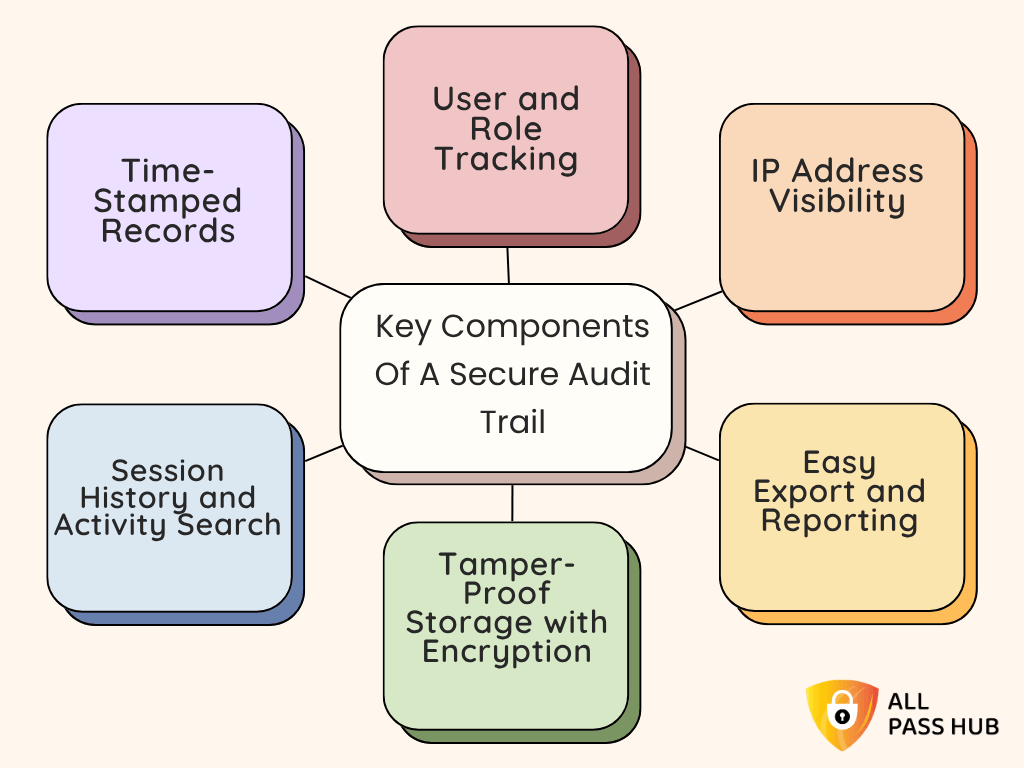
Audit Trails → Track Activity → Compliance Evidence
Imagine a financial auditor asking, “Who accessed this system last Tuesday?” You can only guess without logs. Audit trails answer those questions instantly.
- Business Value: Creates a tamper-proof record of every login, making compliance checks and investigations far less painful.
Cross-Device Sync → Productivity Anywhere → Smoother Remote Work
In today’s hybrid work culture, a password locked to one device is futile. Cross-device sync ensures consistency in access, whether your team is on a laptop, tablet, or smartphone.
- Business Value: Remote and on-the-go employees stay aligned without creating risky workarounds.
Password Generator → Strong Credentials → Reduced Human Error
Most people still default to “easy-to-type” passwords. A built-in password generator eliminates weak and recycled credentials by creating impenetrable, unique ones for every account.
- Business Value: Lowers the likelihood of breaches caused by human laziness or forgetfulness.
The actual power of these features isn’t in the technology itself, but in the outcomes: top-notch security, smoother workflows, and a culture of accountability. All Pass Hub transforms technical specs into practical advantages that teams can feel in their daily work.
Smart Summary: Security features only matter when they deliver genuine results. From encryption to role-based access, All Pass Hub ties every capability to a tangible business outcome.
How Password Managers Protect Company Data
Think of your company’s data like a castle. Without the resilient defenses, attackers don’t need to storm the gates; they just find an unlocked door. A corporate password manager like All Pass Hub ensures every entry point is locked, guarded, and monitored.
Let’s walk you through what protection resembles.
Before: Scattered and Vulnerable
- Saving authentication information in spreadsheets, sticky notes, or chat messages.
- Shared accounts with no record of who accessed them.
- Employees are reusing the same login across multiple platforms.
- A single phishing email escalates into a company-wide breach.
After: Centralized and Secure
- Encryption + Zero-Knowledge Policy → Every password is sealed in an encrypted vault that only your team can unlock. Even All Pass Hub cannot view your data.
- Value: Eliminates the risk of provider breaches or insider snooping.
- Password Vault for Enterprises → Instead of scattered credentials, everything resides in one controlled hub.
- Value: Reduces the hassle of lost logins and reinforces supervision for IT admins.
- Secure Sharing of Files & Credentials → Sensitive access is granted with granular permissions, not emailed around in plain text.
- Value: Fosters trust among teams while safeguarding clients, partners, and internal data.
- Audit Logs & Activity Monitoring → Every login and password change is tracked.
- Value: Transparency deters insider misuse and creates compliance-ready records for audits.
- Data Breach Prevention Mechanisms → Tools such as phishing resistance, brute-force blocking, and MFA integration close familiar attack doors.
- Value: Keeps attackers out, even if one employee makes a mistake.
Replacing ineffective password practices with a secure, centralized system ensures your company’s digital castle is no longer a sitting duck. It becomes a fortress where every wall, gate, and guard works in harmony.
Knowledge Drop: A password manager doesn’t just store credentials; it turns scattered risks into a unified defense system. It ensures business data is locked down and compliant.
Collaboration Made Simple: Real Team Use Cases
Collaboration thrives when everyone knows exactly where to find what they need. A team password manager eliminates the friction of scattered logins and replaces them with structured, secure workflows.
Here are some real-world examples that show how All Pass Hub fits seamlessly into daily team life:
Remote Teams
Remote employees often juggle multiple devices and time zones. With All Pass Hub’s cross-device sync, every login is available instantly on desktop, web, or mobile.
No waiting for emails, no hunting in Slack threads. Only secure access when and where required.
Agencies and Consultants
Marketing or branding agencies manage dozens of client accounts across social media apps, ad platforms, and analytics dashboards. A shared vault with role-based access ensures each client’s credentials are safe, organized, and only visible to authorized staff.
Onboarding new consultants is as effortless as assigning them to the secure repository.
HR and IT Departments
HR teams handle sensitive employee records while IT departments safeguard admin credentials for infrastructure. All Pass Hub provides role-based permissions. It ensures HR staff never pry on IT admin passwords, and IT doesn’t access payroll accounts.
Audit logs track every access event for accountability and transparency.
Developers and Designers
From GitHub repositories to design platforms, creative and technical teams use numerous shared accounts. All Pass Hub ensures credentials are rotated regularly, stored securely, and retrieved effortlessly. The result is fewer interruptions and more focus on shipping projects.
Quick Recap: Team password managers do more than store credentials; they enable agencies, IT, HR, and creative teams to collaborate safely without bottlenecks, guesswork, or security gaps.
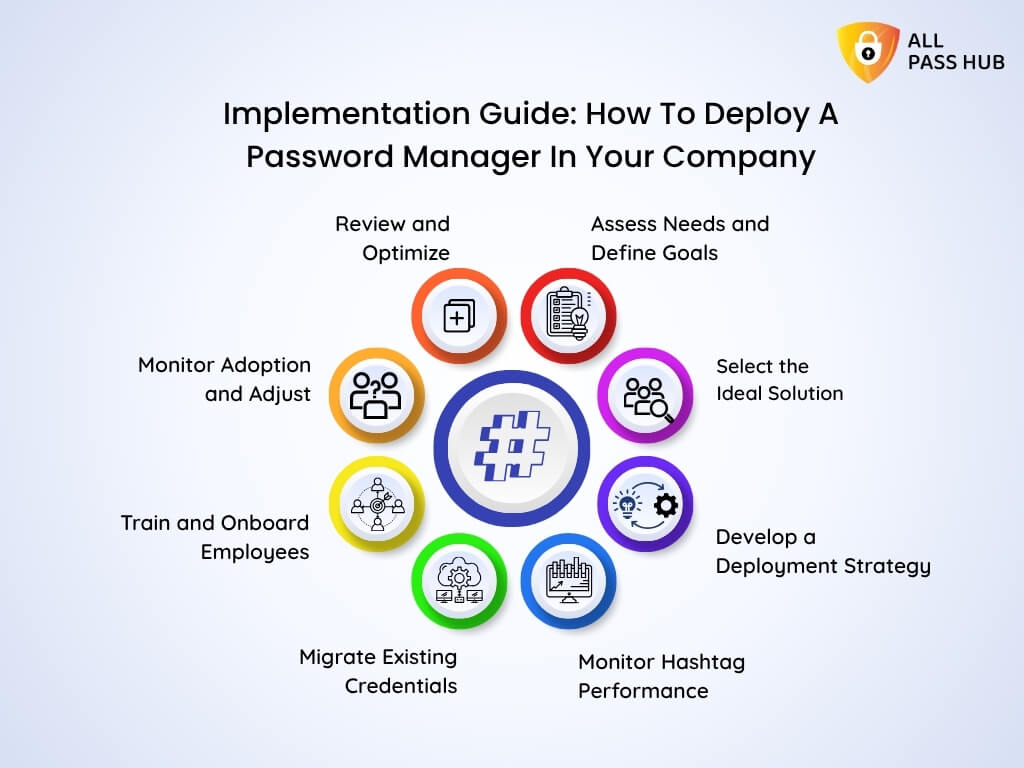
Implementation Guide: How To Deploy A Password Manager For Business
Adopting a team password manager is not just about technology; it is about reshaping how your team treats security every day. A structured rollout ensures smooth adoption, minimal friction, and maximum value.
Here’s a proven path to success:
1. Define an Employee Password Management Policy
Begin by formulating definite rules: how passwords are created, who can share them, and how frequently they must be rotated. This foundation guides every action your team takes inside the password manager.
2. Organize Team Vaults by Department
Create vaults for marketing, HR, IT, development, and client accounts. It prevents clutter, keeps credentials organized, and ensures that employees only access the needed passkeys.
3. Enable MFA and SSO for Stronger Security
Multi-factor authentication combined with single sign-on ensures only verified users can log in. It reduces the risk of compromised accounts while keeping authorization straightforward for employees.
4. Onboard Employees with Training
Guide your team on how to log in, share, and manage credentials inside the repository. A 30-minute training session can prevent months of confusion and hesitation.
5. Use Audit Logs for Continuous Monitoring
Encourage managers and IT admins to check activity logs regularly. It provides visibility into unusual access attempts and ensures compliance requirements are always met.
Must-Know Insight: Successful deployment is about more than installing software. Policies, vault organization, training, and monitoring ensure your password manager becomes a daily security ally rather than another forgotten tool.
Compliance Made Easier With Team Password Managers
Meeting compliance is mandatory for modern businesses. Whether you operate in healthcare, finance, or the e-commerce industry vertical, regulators demand strict controls over the handling of company data and credentials. Failure to comply can invite costly fines, reputational damage, or even legal consequences.
Team password managers like All Pass Hub simplify this challenge. Instead of scattered spreadsheets and unsecured sharing methods, they provide the audit-ready tools enterprises need to pass compliance checks with confidence.
Why Compliance Matters
- GDPR: Requires robust protection of personal data and accountability in access management.
- HIPAA: Demands secure handling of patient information with transparent audit trails.
- SOC 2: Focuses on access control, monitoring, and data confidentiality.
- PCI DSS: Requires safe credential storage and protection for cardholder data.
Feature-to-Compliance Mapping
| Feature | Compliance Need | All Pass Hub Advantage |
| End-to-End Encryption | Data confidentiality (GDPR, HIPAA, PCI DSS) | The zero-knowledge model ensures only authorized users view data |
| MFA + SSO Integration | Strong access controls (SOC 2, PCI DSS) | Multi-layer login protection across teams |
| Audit Trails | Proof of activity and accountability (SOC 2, HIPAA) | Tamper-proof logs track every access event |
| Role-Based Access | Least-privilege principle (ISO 27001, SOC 2) | Permissions set by role to reduce insider risks |
| Centralized Vaults | Secure storage (GDPR, HIPAA, PCI DSS) | Encrypted, organized storage for all credentials |
What This Means For You: Compliance no longer has to be a burden. With features such as encryption, MFA, audit logs, and centralized control, All Pass Hub transforms regulatory pressure into an organized, trackable process.
Common Myths & Risks Without A Team Password Manager
Myths spread faster than facts when it comes to team security. Many companies still hold on to outdated practices, assuming they are “good enough.” Let’s tackle some of the most standard misconceptions head-on.
Myth 1: “A Spreadsheet Will Do the Job”
You might think: “It’s simple, everyone already has access.”
➡️The Truth: Spreadsheets are easily copied, shared, or leaked with no way to trace them. Convenience quickly turns into a security liability.
Myth 2: “A Password Manager Is Too Risky”
You might think: “Why put all my passwords in one basket?”
➡️The Truth: With end-to-end encryption and zero-knowledge design, enterprise password managers ensure no one outside your team, not even the provider, can access your data.
Myth 3: “We’re Too Small to Be a Target”
You might think: “Hackers only go after big companies.”
➡️The Truth: Small teams are often easier targets because their defenses are weaker. A single stolen password can cause disruption, downtime, or reputational loss.
The Hidden Risks of Skipping a Team Password Manager
- Phishing and brute-force attacks thrive on fragile, unmanaged passwords.
- Insider misuse goes unseen without access logs.
- Compliance failures occur when you lack MFA and audit trails.
- Downtime and fines hit harder than the cost of prevention.
In a Nutshell: Relying on outdated methods, such as spreadsheets or ignoring password managers, creates vulnerable spots in your security. The risk is not “if” but “when” an incident will happen.
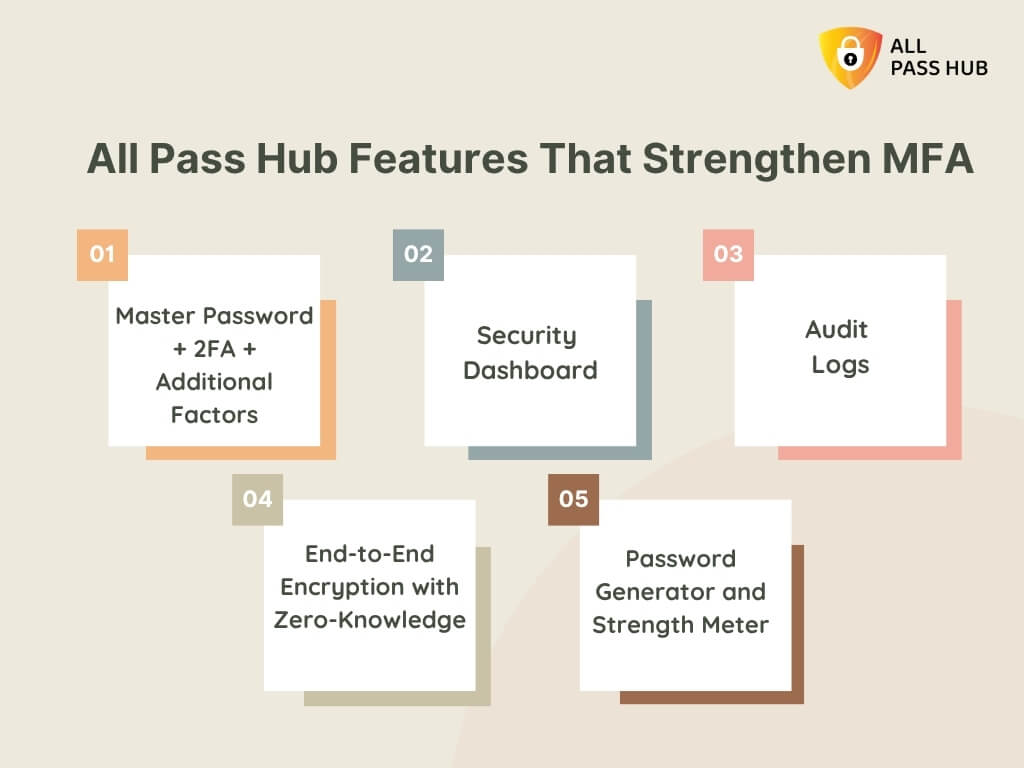
All Pass Hub Features That Teams Love
Flashy features aren’t sufficient when selecting a team password manager. What matters is how those features translate into tangible value for your business, keeping teams secure, productive, and stress-free.
Let’s break down what makes All Pass Hub stand out.
Zero-Knowledge Encryption + AES-128
- Why it Matters: Your credentials are protected with military-grade encryption.
- Value to you: Even All Pass Hub cannot spy on your data, giving you complete privacy and peace of mind.
Multi-Factor Authentication (MFA) and SSO Integration
- Why it Matters: Stronger access control for every login.
- Value to you: Whether logging in through 2FA or integrating with Single Sign-On, your team has additional protection without added friction.
Audit Logs and Compliance Tracking
- Why it Matters: You require visibility into who accessed what and when.
- Value to you: Every action is recorded, helping you meet compliance standards and investigate suspicious activity with confidence.
Cross-Device Sync with Unlimited Users
- Why it Matters: Present-day teams do not work from a single device or one office.
- Value to you: From laptops to mobiles, everyone stays aligned, and you never hit “user limits” that other tools impose.
File Upload & Secure Storage
- Why it Matters: Teams often need to store sensitive documents (contracts, licenses, certificates).
- Value to you: Keep confidential files alongside credentials in one AES-256-bit encrypted vault.
Browser Extension
- Why it Matters: Most breaches happen at the login point.
- Value to you: Autofill securely, save time, and reduce password errors while browsing.
Unlimited Sharing
- Why it Matters: Teams grow, clients change, and authorization needs scale quickly.
- Value to you: Share credentials with as many users as required, without hitting paywalls.
Pin Important Credentials
- Why it Matters: Some logins matter more than others.
- Value to you: Pin your top-used credentials so they are always just a click away.
Search by Tags
- Why it Matters: Large teams can have hundreds of credentials.
- Value to you: Find the right account instantly by using tags like “Finance,” “HR,” “Client A,” or “Vendor A.”
Affordable, Transparent Pricing
- Why it Matters: Security should not be a luxury only large enterprises can pay for.
- Value to you: With All Pass Hub plans ranging from free forever to $0.99/month and $6.99/year, plus enterprise customization, you get world-class security without the premium price tag.
Key Takeaway: All Pass Hub is more than a password manager. It is a scalable, compliance-ready solution designed for real teams, delivering enterprise-grade security without complexity or cost barriers.
Comparison: All Pass Hub vs. Other Team Password Managers
When choosing a password manager for teams, the devil is in the details. Many tools seem identical on the surface, but their limitations often appear only after adoption. Hidden user caps, weak audit logs, or a lack of authentic zero-knowledge protection can quickly turn a promising solution into a frustrating liability.
Here is a transparent comparison between All Pass Hub and other popular team password managers to equip you with clarity:
| Feature / Criteria | All Pass Hub | Typical Competitors |
| Encryption | AES-128 + Zero-Knowledge | Satisfactory but partial provider visibility |
| Role-Based Access | Yes, with granular controls | Limited, often rigid roles |
| Audit Logs | Detailed, tamper-proof, exportable | Basic, often non-exportable |
| Cross-Device Sync | Unlimited devices included | Often, extra charges or limits |
| User Sharing | Limitless at no additional cost | Per-user pricing, capped sharing |
| MFA & SSO Integration | Supported across all plans | Often enterprise-tier only |
| File & Note Storage | Encrypted, integrated with credentials | Basic or unavailable |
| Compliance-Readiness | GDPR, HIPAA, SOC 2, PCI DSS supported | General compliance, fewer specifics |
| Pricing | Free, $0.99/month, $6.99/year, custom enterprise | Higher monthly rates, hidden fees |
➡️What this demonstrates is straightforward: where others restrict, All Pass Hub scales. Where others charge more for enterprise-grade features, All Pass Hub includes them up front. Instead of compromise, you get transparency, affordability, and security in a consolidated vault.
Essential Insight: All Pass Hub outshines competitors with unlimited sharing, tamper-proof logs, and a compliance-first design. It offers transparent pricing without hidden trade-offs.
Building A Culture Of Security And Collaboration
Technology alone cannot safeguard a business; it needs people who understand and adopt secure practices. A team password manager is most potent when it becomes a daily habit rather than a once-a-month IT mandate.
The following are a few practical ways teams can implement to make this shift into their everyday routines.
Encourage Vault-First Habits
Every new credential, whether for a marketing platform or a financial tool, should start in the vault. This habit eliminates scattered spreadsheets and makes security second nature.
Make Security Part of Collaboration
When team members share passwords safely rather than relying on chat messages or sticky notes, they reinforce a culture of trust and accountability.
Scale Security With Growth
All Pass Hub supports unlimited users and affordable tiers, allowing security culture to expand alongside business growth without friction.
Measure and Reward Adoption
Audit logs and activity tracking can highlight departments thriving in guarded collaboration. Recognizing their efforts motivates others to follow suit.
What You Should Know: A culture of security thrives when teams perceive password managers not as tools but as enablers of trust, collaboration, and growth. It makes safe practices effortless across the workplace.
Future Of Team Password Management
The way teams collaborate and protect access is evolving as fast as the threats they face. Password managers are no longer static vaults; they are becoming adaptive guardians that predict risks and simplify workflows.
The future of team password management will be defined by innovation in the following four pivotal areas.
AI-Powered Threat Detection
Artificial intelligence will enable password managers to recognize unusual login patterns, suspicious sharing, or brute-force attempts instantly. All Pass Hub is already aligning toward AI-driven anomaly detection to strengthen team resilience.
Passwordless Authentication and Biometrics
Traditional logins are giving way to biometric authentication and passkeys. Fingerprints, facial recognition, and hardware tokens will soon work seamlessly with team vaults. It will minimize dependency on static credentials.
Next-Generation Vaults for Distributed Teams
As remote and hybrid work are becoming standard, password managers must adapt to support collaboration across geographies. Future vaults will provide real-time sync, offline-ready access, and integrations with emerging workplace platforms.
Compliance in a Post-Quantum World
Stringent regulations and quantum computing threats will push managers to adopt post-quantum cryptography and state-of-the-art compliance automation. Businesses that adopt forward-looking tools now will avoid costly overhauls later.
Final Thought: The future of team password management lies in AI-driven defense, passwordless access, global collaboration support, and post-quantum compliance readiness.
Conclusion
In today’s digital workplace, passwords are more than gatekeepers; they are the keys that unlock collaboration, productivity, and trust. Managing them carelessly turns them into cracks that invite unthinkable threats.
Throughout this guide, you explored how a team password manager replaces chaos with clarity and transforms vulnerability into resilience.
From scattered spreadsheets to centralized vaults, from forgotten logins to streamlined onboarding, and from siloed risks to shared accountability, password managers redefine teams’ working style. They do not just secure credentials; they guard culture, compliance, and confidence.
All Pass Hub is built with this future in mind. With zero-knowledge encryption, MFA, audit-ready logs, and unlimited user scalability, it ensures your team is protected today and prepared for tomorrow’s challenges.
⭐Where others promise, All Pass Hub proves by blending simplicity with enterprise-grade safeguards.
Your business deserves more than fragmented tools. It deserves an armor that evolves with you, protects every interaction, and inspires trust across your teams.
➡️Start your team’s secure journey with All Pass Hub today: collaborate confidently, shield completely.
FAQ
Can A Team Password Manager Integrate With Tools Like Slack Or Google Workspace?
Yes. Many team password managers, including All Pass Hub, integrate with business tools such as Slack, Google Workspace, and project management platforms. It makes credential sharing seamless and lowers the risk of employees resorting to insecure methods such as chat messages or spreadsheets.
How Do Password Managers Handle Employees Who Leave The Company?
A team password manager empowers admins to revoke access instantly when an employee departs. It prevents lingering access to shared accounts and safeguards sensitive data. With centralized control, businesses can transfer or reassign credentials securely without disruption.
What Is The Difference Between A Team Password Manager And A Password Vault?
A password vault is primarily a secure storage for credentials, whereas a team password manager combines vaulting with collaboration features, such as role-based access, audit logs, and safe sharing. It makes it practical for businesses requiring superior oversight and control.
How Does A Password Manager Improve ROI For Businesses?
Password managers save both time and money by reducing password reset requests, eliminating downtime caused by lost credentials, and lowering the risk of breaches. Productivity gains and compliance-readiness add further long-term ROI for companies of all sizes.
Is There A Risk Of Losing Access If The Password Manager Fails?
Reputable password managers provide secure recovery options, such as encrypted recovery files or admin reset controls. It ensures businesses retain access even if users forget master credentials, without compromising the zero-knowledge security model.
Do Small Teams And Agencies Really Need A Password Manager?
Yes. Even small teams face threats from password reuse, insecure sharing, and accidental leaks. A team password manager offers affordable, scalable protection that grows with the business. For agencies handling multiple clients, it provides clear separation and secure access control for each project.