- Posted on October 13, 2025
- 19 Min Read

Here’s a reality check that stings: Nearly 81% hacking-related breaches in corporate settings still trace back to weak, reused, or stolen passwords. Attackers no longer need to break into vaults with brute force; they trick, phish, and exploit human errors quicker than ever before.
Relying on a single password in today’s digital landscape is like locking your front door but leaving the windows wide open.
So, how can individuals, teams, and enterprises safeguard their credentials when cybercriminals constantly raise the stakes? The answer lies in multi-factor authentication (MFA), a digital security authentication method that adds layers of protection.
It turns a stolen password into nothing more than an ineffective string of characters. MFA is a lifeline for businesses, high-performance teams, and anyone serious about defending their digital presence.
In this blog, you’ll discover what multi-factor authentication is, how it works, why it is paramount in 2025, and how All Pass Hub strengthens MFA with encryption, audit logs, and seamless team collaboration.
You’ll also explore real-world benefits, best practices, recovery strategies, and the future of authentication.
Get ready to see how MFA reshapes password security, and why adopting it with All Pass Hub could be the wisest move you make this year.
What Is Multi-Factor Authentication (MFA)?
At its core, multi-factor authentication is about confirming that the person accessing an account is actually its rightful owner. Instead of relying on a single lock, MFA adds extra doors, keys, and checkpoints that hackers cannot easily bypass.
It blends convenience with security, creating a layered defense that has become crucial in today’s connected world.
Breaking It Down Simply
- Knowledge (something you know): A password or PIN.
- Possession (something you have): A phone with an authenticator app or a hardware token.
- Inherence (something you are): Biometric markers such as a fingerprint or facial recognition.
When two or more of these factors are combined, the odds of a cybercriminal breaking in drop dramatically. Even if your password is stolen, attackers face the impossible task of faking your phone, fingerprint, or both.
MFA vs 2FA
Two-factor authentication (2FA) uses exactly two factors, such as a password plus a one-time code. MFA can include two, three, or more verification layers. Think of it as upgrading from a sturdy lock to an entire security system with motion sensors, cameras, and alarms.
That is why teams and businesses are moving beyond password-only models. Stolen credentials no longer spell disaster when MFA is in place. Instead, they become a dead end for attackers.
Main Message: Multi-factor authentication blends knowledge, possession, and inherence to build resilience. Unlike password-only setups, it provides a layered shield that keeps individuals, teams, and enterprises one step ahead of the latest cyber threats.
Read More: – Password Manager for Team
How Does Multi-Factor Authentication Work?
The easiest way to picture multi-factor authentication in action is to imagine entering a high-security building.
- First, you swipe your badge (a password).
- Then, you punch in a unique code sent to your phone (verification code).
- Finally, you place your finger on a scanner (biometric factor).
👉Note: Access is permitted only when all three are aligned.
Steps Involved In MFA
This step-by-step approach creates multiple roadblocks for attackers:
- Step 1: Password – your first line of defense, but vulnerable if stolen.
- Step 2: Verification code – time-sensitive and linked to your personal device.
- Step 3: Biometric factor – nearly impossible to replicate, unique to you.
Real-World MFA Examples
- Authenticator apps such as Google Authenticator or Authy generate one-time codes.
- Tokens issue rotating codes or push notifications.
- Biometric checks, such as Face ID or fingerprints, safeguard mobile and desktop logins.
Adaptive MFA: Risk-Based Authentication
Modern systems leap with adaptive MFA. Rather than treating every login the same, they assess risk factors such as location, device, or time of access.
➡ ️ For example, if a user suddenly logs in from a new country at 2 AM, the system might demand an additional factor before granting entry. This flexibility fortifies protection without overburdening users.
In a Nutshell: Multi-factor authentication works by layering knowledge, possession, and inherence. It is often enhanced by adaptive checks to block attackers even when one factor is compromised.
Read More:- Best Zero-Knowledge Password Manager
MFA Benefits For Teams & Businesses
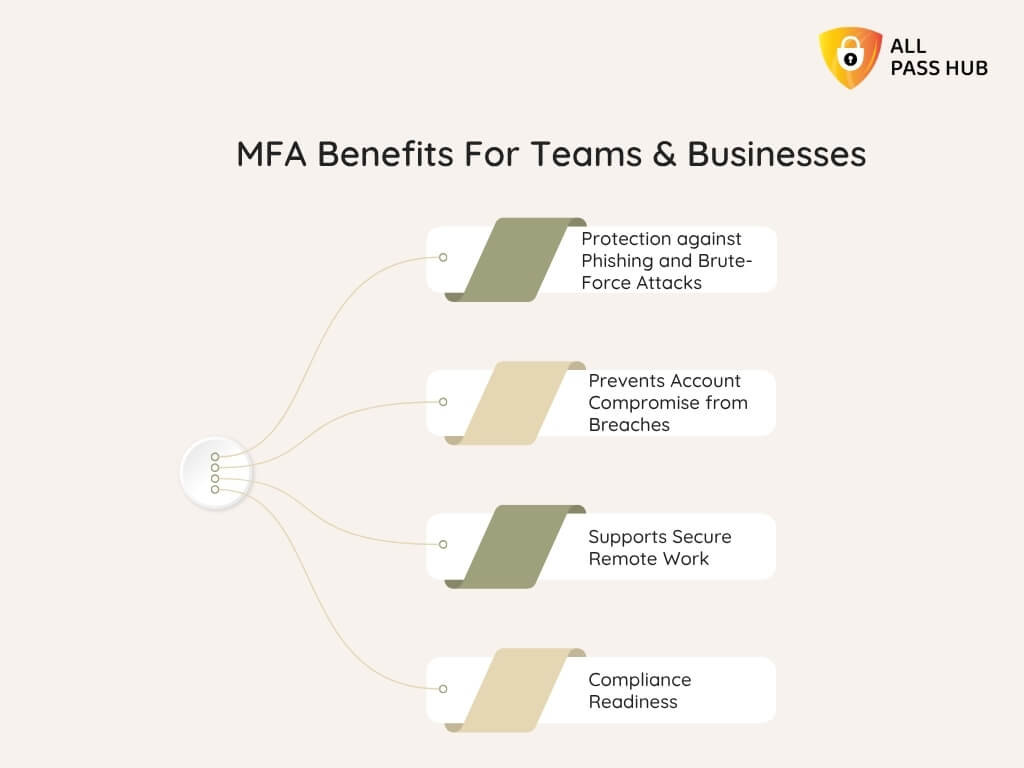
Cyber threats are no longer a distant danger; they strike daily, often without warning. One stolen password can expose an entire company’s data. However, multi-factor authentication builds an unbreakable protection wall that transforms this risk into reassurance.
Why MFA Matters For Businesses And Teams
- Protection against Phishing and Brute-Force Attacks: MFA keeps hackers locked out even if they trick someone into revealing their password.
- Prevents Account Compromise from Breaches: Credentials leaked in data breaches lose their power when extra factors are required.
- Supports Secure Remote Work: With employees signing in from multiple devices and locations, MFA ensures every login is verified.
- Compliance Readiness: Many industries now mandate MFA to meet security regulations, making it both a defensive and legal necessity.
For enterprises, this translates into fewer breaches, smoother compliance audits, and measurable cost savings. For teams, it fosters trust by ensuring collaboration happens in a safe environment. For individuals, it means peace of mind that their personal data remains private in the scenario of password theft.
Core Insight: Multi-factor authentication safeguards businesses, teams, and individuals by preventing breaches, strengthening compliance, and ensuring peace of mind in today’s unpredictable digital world.
Read More:- Best Password Manager for High-Performance Teams
All Pass Hub Features That Strengthen MFA
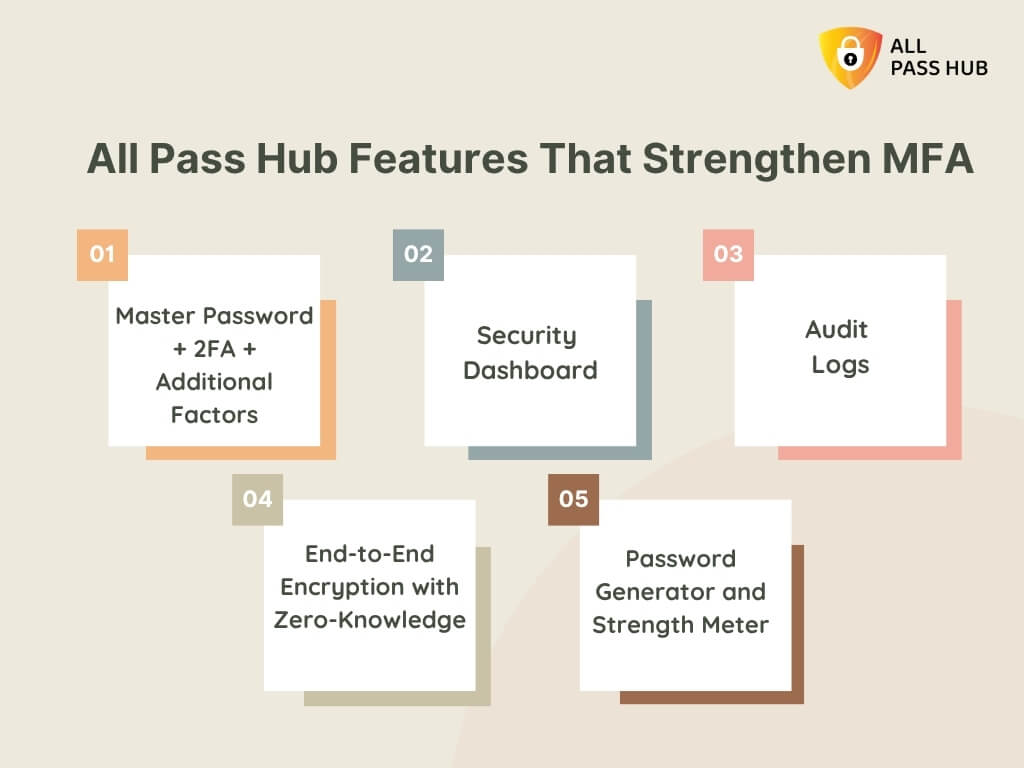
Understanding multi-factor authentication in theory is one thing, but seeing it put into practice through All Pass Hub shows just how potent it becomes when paired with groundbreaking security tools. All Pass Hub takes MFA beyond the basics, building layers of defense that support both individuals and enterprises.
How All Pass Hub Enhances MFA
- Master Password + 2FA + Additional Factors: Every login requires multiple verifications, ensuring stolen credentials alone cannot open the vault.
- Security Dashboard: Address issues instantly by flagging weak or compromised passwords before attackers exploit them.
- Audit Logs: Provide transparency into login attempts, highlighting suspicious access patterns and reinforcing MFA enforcement.
- End-to-End Encryption with Zero-Knowledge: All authentication data is encrypted locally, ensuring that not even All Pass Hub can view user credentials.
- Password Generator and Strength Meter: Prevent weak entry points by encouraging resilient, unique passwords before MFA layers are added.
This combination means MFA with All Pass Hub is not just a safety net; it is a pivotal component of a complete ecosystem aimed to shield every login, team member, and shared credential.
Knowledge Drop: All Pass Hub elevates MFA by combining strong encryption, real-time dashboards, and transparent audit logs. It creates a layered security system personalized for individuals, teams, and enterprises.
Read More – Hidden Features Of All Pass Hub
MFA In Action: How Teams Use All Pass Hub
Theory becomes truly valuable when it translates into everyday protection. That’s where All Pass Hub’s multi-factor authentication shines. It is not just a security setting buried in the background; it is a daily ally for teams, enterprises, and individuals managing sensitive credentials.
Let’s look at how this plays out in real-world scenarios.
Remote Teams Accessing Cloud Apps
Picture a marketing team spread across three continents. They need to access social accounts, analytics dashboards, and project tools every day. Even if a member’s password is phished, attackers cannot break into company resources with MFA in place.
Each login is verified, giving managers peace of mind that global access does not equal global risk.
Enterprises Enforcing Role-Based Access
Enterprises handle several employees, contractors, and partners. All Pass Hub allows administrators to enforce MFA at scale, assigning access levels based on roles.
Finance cannot view IT credentials, and interns have restricted access to executive tools. MFA ensures that sensitive systems are safeguarded behind multiple checks.
Collaboration And Credential Sharing
Agencies and startups often need to share client logins or internal tools among teams. With MFA in place, you can securely share credentials without fear of leaks.
Every access attempt is logged, time-stamped, and verified. It creates an audit trail that guards both users and organizations.
Must-Know Insight: All Pass Hub brings MFA to life by protecting remote teams, enforcing role-based access, and enabling safe credential sharing. It turns collaboration into a secure and transparent process.
2FA vs MFA: What’s the Difference?
Many people confuse two-factor authentication (2FA) with multi-factor authentication (MFA), and even use them interchangeably. Though they sound similar, the protection they offer is not identical. Both add layers beyond passwords, yet MFA offers broader flexibility and stronger resilience for enterprises and teams.
Here’s a clear comparison:
| Aspect | 2FA (Two-Factor Authentication) | MFA (Multi-Factor Authentication) |
| Number of Factors | Exactly two (password + one additional factor) | Two or more (password + code + biometrics, tokens, or more) |
| Examples | Password + SMS code | Password + Authenticator App + Fingerprint |
| Flexibility | Limited, only two checks possible | Highly flexible, can combine multiple authentication factors |
| Security Strength | Stronger than passwords alone but limited if one factor is compromised | Significantly stronger, harder for attackers to bypass multiple diverse factors |
| Use Cases | Common for personal accounts like email or banking | Ideal for enterprises, remote teams, and compliance-heavy industries |
| Future Alignment | Suitable but may struggle against evolving threats | Adaptive, aligns with biometrics, passkeys, and AI-driven authentication trends |
👉Note: 2FA adds an extra safety, and MFA installs an entire security system. MFA is a clear-cut choice for organizations handling sensitive credentials or aiming for compliance.
The Bottom Line: While 2FA improves security, MFA offers top-notch flexibility and higher protection by blending multiple authentication factors. It makes it the gold standard for modern businesses and teams.
Read More:- Enterprise Password Manager for CTOs and Admins
Best Practices For MFA Implementation
Multi-factor authentication delivers unbreakable protection only if it is implemented thoughtfully and used consistently. Without proper planning, teams risk confusion, weak adoption, or gaps in coverage. The good news is that following a few best practices ensures MFA runs smoothly across businesses of any size.
Practical Checklist For MFA Success
✅Train Employees on Consistent Use: Educate staff on why MFA matters and how to adopt it across devices, apps, and shared credentials. Awareness builds cooperation.
✅Create an MFA Adoption Checklist: Define required accounts, apps, and services that must have MFA enabled. It avoids partial coverage and vulnerable points.
✅Use Audit Logs for Oversight: Monitor unusual login attempts, privilege escalations, or repeated failures to fortify security.
✅Monitor the Security Dashboard: Obtain real-time alerts on weak credentials and suspicious activities. It helps to detect problems before they escalate.
✅Customize MFA for Small Businesses: Smaller teams may start with a master password plus an authenticator app. Gradually scale into biometrics or tokens as needs grow.
When done correctly, MFA not only protects data but also fosters trust. Teams feel safer, compliance becomes easier, and leaders can rest assured that their defenses are proactive rather than reactive.
Essential Insight: Rock-solid MFA adoption begins with training, clear checklists, and real-time monitoring. It ensures every login is verified and every team member plays a pivotal role in digital security.
Common Risks And Challenges Without MFA
Relying solely on passwords today is like leaving your vault wide open while hoping thieves will not notice. Businesses, teams, and individuals encounter risks that are both immediate and severe without multi-factor authentication.
What Can Go Wrong Without MFA
- Phishing Attacks Succeed More Easily: A single careless click can expose login details. And without MFA, attackers walk straight into accounts.
- Brute-Force Attempts Crack Logins: Automated tools can try millions of password combinations, breaking through weak defenses in minutes.
- Insider Misuse Goes Unchecked: Employees or contractors with malicious intent can exploit shared credentials without additional verification.
- Compliance Gaps Add Liability: Industries bound by SOC 2, HIPAA, or GDPR may face fines or audit failures if MFA is not enforced.
- False Assumptions Delay Action: Many still think MFA is “too complex” or “only for large enterprises,” leaving them vulnerable to attacks they could have prevented.
💡Pro Tip: The cost of ignoring MFA is not just financial; it includes damaged reputations, lost clients, and disrupted operations. Hackers thrive on simplicity, and a password-only environment is the most straightforward target of all.
What You Should Know: Without MFA, phishing, brute-force attacks, insider misuse, and compliance failures become everyday risks. It makes businesses vulnerable to breaches that could have been easily prevented.
Compliance & Regulatory Landscape In 2025
Regulators and standards bodies are enforcing organizations to tighten access controls, and multi-factor authentication has shifted from best practice to an explicit requirement in some contexts.
Below is a practical map of what key frameworks to expect in 2025 and how MFA fits into each one.
| Standard / Law | MFA Expectation (2025) | What It Means In Practice |
| PCI DSS (Payment Card Industry) | MFA is required for all access to the cardholder data environment (CDE) and most remote or privileged access. | Implement MFA for all CDE access, cloud components, admin logins, and remote access; no bypass allowed. Evidence of MFA controls is required during assessments. (PCI Compliance Hub) |
| HIPAA (U.S. Health Data) | Becoming mandatory under proposed Security Rule updates, OCR has signaled MFA will be required with limited exceptions. | Covered entities and business associates should prepare to enforce MFA for access to ePHI, including stronger recovery procedures and documented risk analyses. Monitor final rule text and compliance timelines. (HHS.gov) |
| SOC 2 (Trust Services Criteria) | Strongly recommended as a control to meet the Security principle; not always spelled out as a strict mandate. | Use MFA to demonstrate effective access controls and reduce unauthorized access. Auditors will expect MFA where risk analysis shows it is appropriate. (Secureframe) |
| GDPR (EU Data Protection) | Not explicitly mandatory, but required as an appropriate technical measure for high-risk access to personal data. | Apply MFA where the risk to personal data is significant. Document why MFA is used and how it aligns with the data protection impact assessment and technical measures requirement. (Secret Double Octopus) |
How Organizations Should Act Now
- Treat MFA as a baseline control for any privileged, remote, or high-risk access. Evidence of implementation will be critical in audits and incident investigations.
- Align MFA rollouts with risk assessments, compliance calendars, and vendor contracts. With rules still evolving, document your risk-based decisions and timelines.
- Build audit trails that show MFA enforcement and exceptions to demonstrate controls during SOC 2 audits or regulatory reviews.
What You Should Know: MFA is now an essential control for payment environments. It is rapidly becoming mandatory or necessary across healthcare, SOC 2, and privacy frameworks. Ensure to prepare, document, and prove your MFA controls.
Recovery And Fallback Design: Staying Accessible
Even the strongest multi-factor authentication system must address an unavoidable reality: people lose devices, reset phones, or get locked out of their authenticators. Without a recovery plan, MFA can backfire by locking out legitimate users and slowing down teams when every minute is crucial.
Regulators like SOC 2 and HIPAA emphasize not only secure access but also continuous availability. It means fallback methods must keep people working without weakening security.
Here’s how organizations can balance both:
Practical Recovery Measures
- Backup Codes: Provide one-time, limited-use codes stored securely offline.
- Secondary Factors: Allow trusted devices, biometrics, or hardware tokens as alternate verifications.
- Role-Based Approval: Empower admins to re-verify users through documented approval, with all activity logged.
- Training Employees: Teach staff to follow safe recovery protocols, avoiding shortcuts such as email-only resets.
- Audit Trail Recording: Ensure every recovery attempt is recorded. It indicates to regulators and auditors that proper oversight exists.
Why It Matters For Compliance
- SOC 2 and PCI DSS: Expect to see proof of fallback processes that don’t weaken security.
- HIPAA: Requires continuity of access to patient data; recovery plans prevent disruption in care.
- GDPR: Stresses accountability, so fallback processes must be secure, documented, and justifiable in audits.
Key Takeaway: A well-structured recovery plan avoids business disruptions while meeting compliance requirements. Reliable fallback keeps users working, regulators reassured, and attackers locked out.
All Pass Hub vs Other MFA Solutions
It’s natural to get lost in similar-sounding features when selecting a multi-factor authentication tool. However, not every solution is built to scale across individuals, teams, and enterprises with the same harmony of security, usability, and transparency.
All Pass Hub sets itself apart by weaving MFA directly into a broader ecosystem of secure password management, credential sharing, and audit oversight. While others may stop at token-based logins or app codes, All Pass Hub surpasses with role-based controls, encrypted audit trails, and compliance-ready safeguards.
Here’s how All Pass Hub compares against common alternatives:
| Feature | All Pass Hub | Standard MFA Solutions | Other Password Managers |
| Authentication Options | Master Password + 2FA + additional MFA (biometric, authenticator app, tokens) | Typically limited to 2FA via SMS or authenticator app | Basic 2FA only |
| Audit Logs | Detailed, tamper-proof logs with IP, timestamp, and role context | Rarely included | Limited or not transparent |
| Team Enforcement | Centralized MFA enforcement for all users, role-based access | Manual enforcement, often per user | Some role options, weaker visibility |
| Security Dashboard | Alerts on weak, reused, or compromised credentials | Not usually included | Basic reporting only |
| Encryption Standard | End-to-end AES-128 with zero-knowledge design | Varies; some partially store data on servers | Often AES-256, but without true zero-knowledge |
| Compliance Readiness | SOC 2, GDPR, HIPAA, and PCI DSS are aligned with audit trails | Minimal compliance focus | Limited industry-specific coverage |
| Scalability | Unlimited team members without extra cost | Often licensed per user | Premium tiers restrict user counts |
| Recovery and Fallback | Backup codes, role-approved recovery, full audit of resets | Limited fallback, often insecure email reset | Inconsistent across platforms |
| Value Proposition | Unified solution: sync, share, MFA, logs, compliance in one | MFA only, siloed | Partial overlap, higher costs for enterprises |
➡️Why It Matters: Instead of bolting MFA on as an afterthought, All Pass Hub makes it an integrated, compliance-ready safeguard. It saves time, lowers costs, and delivers peace of mind for every user, from freelancers to global enterprises.
The Crux: All Pass Hub is not just another MFA tool. It is a comprehensive, transparent, and scalable security solution that ensures seamless and secure collaboration.
Future Of Multi-Factor Authentication
Cybersecurity is not static. Attackers become more cunning as technology evolves, and what feels cutting-edge today may become outdated tomorrow. That is why multi-factor authentication must continue to adapt.
The future of MFA is not just about adding more layers; it is about making them smarter, faster, and invisible to friction-prone workflows.
Emerging Trends To Watch
- AI-Driven Authentication: Artificial intelligence will examine user behavior patterns such as typing rhythm, device fingerprint, or login location to flag anomalies instantly.
- Passkeys vs MFA: Passkeys are gaining traction as a passwordless option, and they will be linked to device-based cryptography. While convenient, MFA remains integral when layered with other factors to defend against device theft or phishing.
- Biometric Authentication Evolution: Facial recognition, fingerprint scans, and even voiceprints will grow more reliable, with fallback systems ensuring users never get locked out.
- Post-Quantum Cryptography: With quantum computing threatening traditional encryption, MFA will correspond with stronger cryptographic algorithms to remain resilient.
- Contextual MFA: Instead of triggering MFA at every login, systems will adapt based on context, such as high-risk locations, devices, or unusual behavior.
Why This Matters For Businesses
Enterprises cannot afford to wait for these shifts to become mainstream. By adopting a password manager that evolves with future standards, they ensure that security investments remain effective today and tomorrow.
All Pass Hub is already moving toward this future. It combines zero-knowledge design, role-based enforcement, and audit-ready transparency with a roadmap that embraces biometric growth, AI-driven monitoring, and integration with upcoming encryption standards.
Final Thought: The future of MFA is about staying ahead of threats with intelligent, adaptive, and quantum-resistant defenses. All Pass Hub ensures your team is always prepared for what comes next.
Conclusion
Passwords alone are no longer enough to protect what matters most. From phishing emails to brute-force attacks, digital threats have grown sharply and rapidly, leaving single-password defenses exposed. That is why multi-factor authentication has moved from a “nice-to-have” to a true non-negotiable feature.
Throughout this guide, you’ve explored what MFA is, how it works, and why it matters for businesses, teams, and individuals.
You also discovered how All Pass Hub pairs MFA with other potent safeguards such as end-to-end encryption, zero-knowledge design, audit trails, and role-based access. The result is a solution that balances robust protection with effortless usability.
Whether you are a startup building trust with your first customers, a remote team juggling collaboration across time zones, or an enterprise facing stringent compliance demands, the same truth applies: MFA with All Pass Hub protects your world without slowing it down.
➡️Now is the time to step into a safer, more transparent future. Choose All Pass Hub and give yourself the peace of mind, compliance assurance, and confidence to thrive in 2025 and beyond.
FAQ
Can MFA Stop Phishing Attacks?
Yes, MFA blocks most phishing attempts by requiring additional verification beyond stolen credentials. Even if an attacker has a password, they cannot bypass the second or third authentication factor.
How Does MFA Integrate With Password Managers?
Password managers like All Pass Hub combine strong vault encryption with MFA. This means users must authenticate not just with a master password, but also with an additional factor, such as an app, token, or biometric.
What Are The Three Factors Of Authentication?
They are: something you know (password), something you have (smartphone or token), and something you are (biometric, such as fingerprint or face scan). MFA combines two or more factors to strengthen identity verification.
Is MFA Required For Compliance Audits?
Yes, frameworks such as SOC 2, HIPAA, GDPR, and PCI DSS expect MFA for access to sensitive systems. Regulators see MFA as an essential safeguard for reducing unauthorized access risk.
How Do I Train My Employees To Adopt MFA?
Provide simple setup guides, run brief awareness sessions, and explain why MFA matters. Reinforce with reminders, mock phishing tests, and ensure IT support is ready to help with enrollment.
Is MFA Secure Enough Against AI-Driven Threats?
MFA adds resilience against AI-powered attacks by introducing barriers beyond credentials. Adaptive MFA, which adjusts security based on risk, further reinforces defenses against automated intrusion attempts.
How Do Passkeys Compare With MFA?
Passkeys eliminate traditional passwords by using device-based cryptography. Though they reduce phishing risks, they are still evolving. MFA remains widely adopted, flexible, and can work alongside passkeys for multi-layered security.
What Happens If I Lose Access To My MFA Device?
Most solutions, including All Pass Hub, offer secure recovery through backup codes or admin-approved reset processes. Recovery protocols aim to keep accounts accessible without compromising security.
Does MFA Slow Down Daily Workflows?
Advanced MFA methods, such as biometrics and push notifications, add only a few seconds to the login process. In return, they prevent costly breaches and downtime, making them far more efficient than relying solely on passwords.