- Posted on October 2, 2025
- 19 Min Read

In 2025, billions of passwords are traded on underground forums every month, and even companies with strict IT policies face breaches that cost millions of dollars.
➡️Have you ever wondered why so many businesses and individuals still struggle to keep credentials safe in today’s AI-dominating landscape? The answer is: traditional password security methods. Though they were once sufficient, they can no longer withstand the scale of cyberattacks, regulatory pressures, and insider risks.
That is why we have designed this blog for professionals, enterprises, and everyday users who want to understand what zero-knowledge architecture and end-to-end encryption password solutions are, and why they matter in the current era.
You will also discover how these advanced security layers create a vault where only you hold the keys, why conventional password encryption methods are outdated, and how to choose the best password managers with zero-knowledge to safeguard data.
The journey ahead explains the architecture, the protection lifecycle, real-world benefits, and the unique way All Pass Hub delivers zero-knowledge architecture security you can trust.
Let’s get started!
What Is Zero-Knowledge Encryption, And Why It Matters
If traditional password encryption feels like locking valuables in a safe that someone else has a spare key to, zero-knowledge encryption removes that spare key altogether.
The only person who can ever access your vault is you. This is why businesses and individuals searching for resilient password security architecture turn to solutions built on zero-knowledge design.
So, how does zero-knowledge encryption work in password managers?
- Your master password never leaves your device.
- Instead, it is converted into a unique encryption key locally.
- That encryption passkey protects your vault before anything reaches the servers.
- Even if attackers gained access to servers, they would see only unreadable ciphertext.
What makes zero-knowledge encryption tamper-proof and hard to hack is its absolute separation of control. No third party can read, reset, or reveal your stored information. This model prevents both external breaches and insider threats, giving users genuine ownership of their data.
That is why All Pass Hub integrates zero-knowledge encryption at its foundation, ensuring your vault remains private, uncompromised, and accessible only to you.
Main Message: Zero-knowledge encryption keeps control in your hands by ensuring your master password never leaves your device. It creates a vault that cannot be exposed by providers, hackers, or unauthorized insiders.
How Zero-Knowledge Architecture Security Works In All Pass Hub
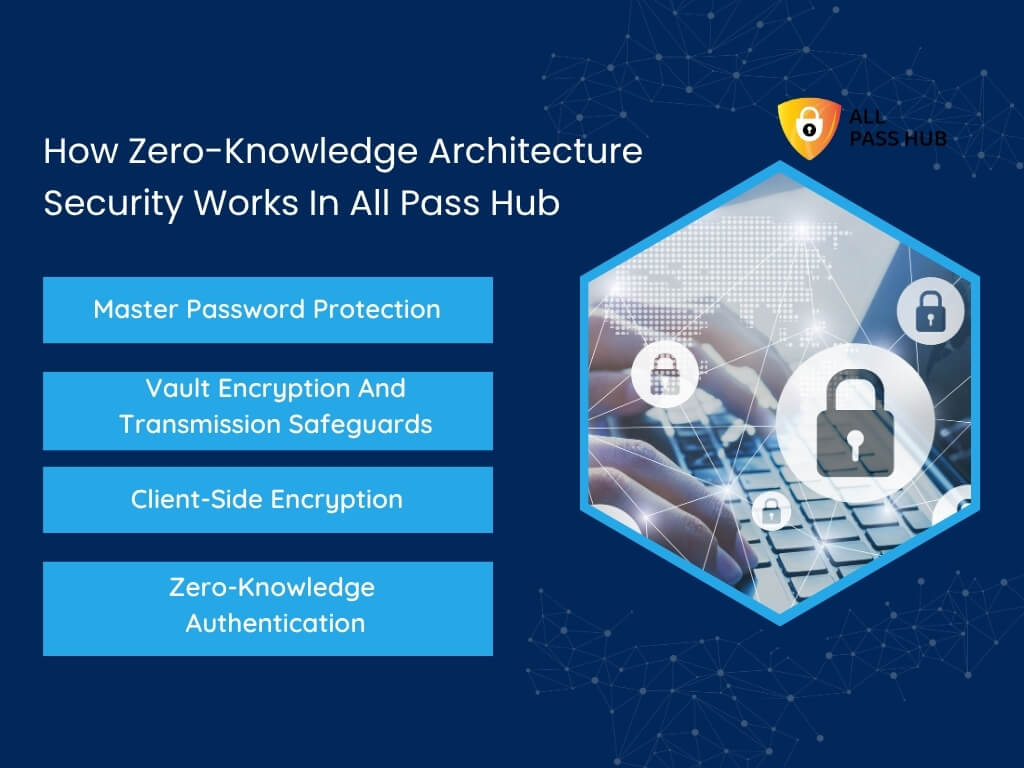
Understanding theory is helpful, but knowing how zero-knowledge encryption actually functions in practice equips you with clarity and confidence. All Pass Hub’s zero-knowledge architecture security is built on tested cryptographic elements designed to shield every password in your vault.
Let’s break it down into its pivotal components to see how it works step by step.
Master Password Protection
- All Pass Hub uses PBKDF2-SHA256 with 600,000 iterations to transform your master password into an encryption construct.
- This high iteration count makes brute-force attempts computationally impractical.
Vault Encryption And Transmission Safeguards
- Data at rest is secured with AES-128, a military-grade algorithm trusted worldwide.
- Every transaction in transit is shielded with TLS 1.2+, preventing interception.
Client-Side Encryption For Total Ownership
- Sensitive data is encrypted on your device before it is transmitted to servers.
- Even All Pass Hub’s systems cannot decipher your vault, maintaining complete confidentiality.
Zero-Knowledge Authentication Construct
A separate authentication layer, derived from an additional iteration, validates access.
This dual-layer approach ensures that authentication and decryption remain wholly distinct.
➡️The outcome is a vault designed for privacy and resilience, where even service operators cannot interfere with your information.
Core Insight: All Pass Hub safeguards your vault with PBKDF2-SHA256, AES-128, TLS 1.2+, and client-side encryption, combining layered defenses into a zero-knowledge architecture that gives you firm control.
What Is End-To-End Encryption (E2EE) Explained Clearly
If zero-knowledge encryption guarantees that only you can read your vault, end-to-end encryption ensures that every step of communication remains guarded from start to finish. It means your data is already encrypted on your device before it ever moves across networks, and it only gets decrypted when you decide to open it.
To understand how this works in password protection, let’s discuss its vital elements.
Layperson Understandable Definition
- End-to-end encryption password protection means only the sender and the intended recipient can access readable information.
- No third-party, not even the service provider, can view the unencrypted content.
Dual-Layer Defense With Two Constructs
- Your login password authenticates access to the system.
- A separate master key decrypts your vault data. Even if one element is compromised, your credentials remain safeguarded.
Comparing Password Encryption Methods
- Traditional methods encrypt data but often allow recovery access through provider-managed keys.
- End-to-end encryption eliminates this dependency, removing backdoors that could expose sensitive data.
Real-World Examples
- Messaging apps, such as Signal or WhatsApp, leverage E2EE to block interception.
- Password managers, such as All Pass Hub, apply the same principle to vaults, ensuring credentials remain confidential.
- Secure file-sharing services rely on E2EE to protect documents in transit.
By combining dual-layer defense with encrypted communication pathways, end-to-end encryption delivers confidentiality without compromise.
What This Means For You: End-to-end encryption protects your vault by encrypting data before it leaves your device and decrypting it only on your side. It eliminates exposure risks and ensures total privacy in every interaction.
End-To-End Encryption vs. Zero-Knowledge: Key Differences
Now that we understand how end-to-end encryption and zero-knowledge encryption function individually, let’s compare the two. Many readers wonder if they serve the same purpose or if one is superior to the other.
The truth is that they complement each other, and together they form the foundation of a trustworthy password security architecture.
Let’s break down how they differ and why combining them is necessary.
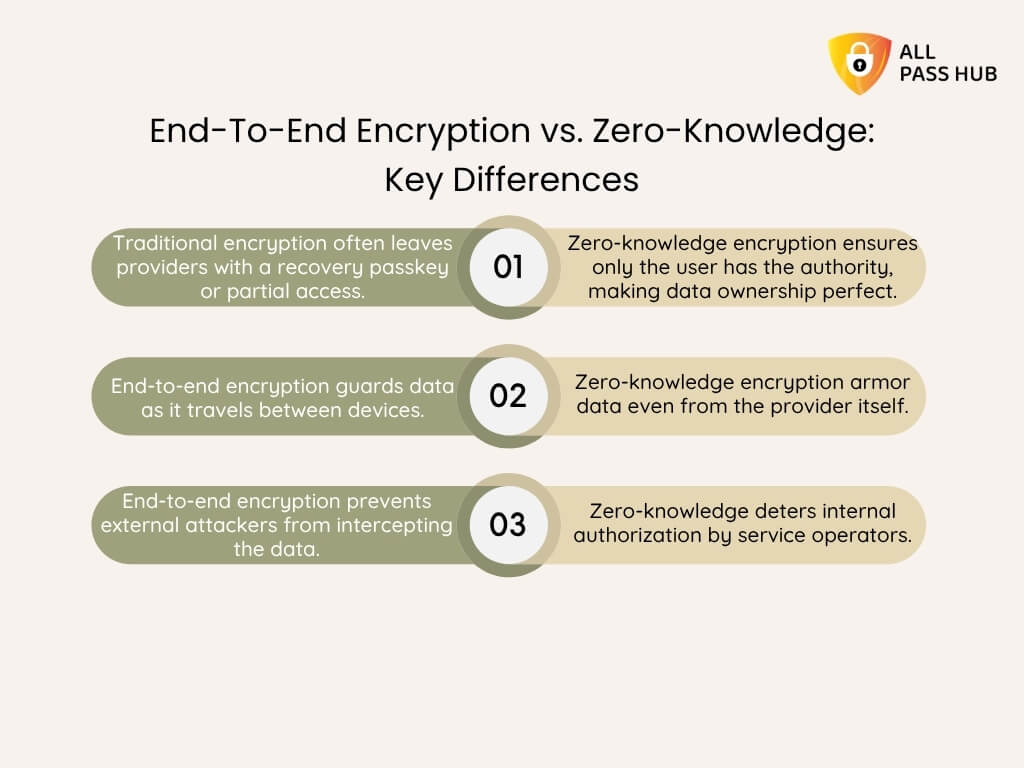
Zero-Knowledge vs. Traditional Encryption
- Traditional encryption often leaves providers with a recovery passkey or partial access.
- Zero-knowledge encryption ensures only the user has the authority, making data ownership perfect.
End-To-End Encryption vs Zero-Knowledge In Practice
- End-to-end encryption guards data as it travels between devices.
- Zero-knowledge encryption armor data even from the provider itself.
Combined, they protect your vault both in transit and at rest.
Why Does Pairing Them Create Resilient Protection
- End-to-end encryption prevents external attackers from intercepting the data.
- Zero-knowledge deters internal authorization by service operators.
Together, they create a complete wall of privacy that traditional models cannot match.
A Visual Glance At How They Differ
| Aspect | End-to-End Encryption | Zero-Knowledge Encryption |
| Definition | Protects data as it travels between devices. | Armor data, even from the service provider itself. |
| Primary Role | Shield information in transit from interception. | Ensures only the user can access and decrypt vault data. |
| Traditional Weakness Addressed | Prevents man-in-the-middle attacks and network interception. | Eliminates provider backdoors and insider access risks. |
| Data at Rest vs Transit | Focuses on encryption during transmission. | Focuses on vault storage and authentication privacy. |
| Recovery Options | Limited, as providers do not retain readable copies. | No provider-based recovery, only user-managed control. |
| Combined Benefit | Ensures secure delivery of data. | Guarantees exclusive ownership of stored data. |
This is why All Pass Hub integrates both zero-knowledge architecture security and end-to-end encryption in its platform. It ensures data remains private across every stage of its lifecycle.
In a Nutshell: End-to-end encryption secures your data in transit while zero-knowledge ensures providers cannot access it. Together, they form a unified defense that keeps vaults confidential in every scenario.
Full Lifecycle Protection: From Password Creation To Deletion
Passwords are not static. They pass through different stages, from creation to storage, sharing, retrieval, and eventual deletion or rotation. An authentic password security architecture must protect at every stage of this journey.
Let’s walk through each step to see how zero-knowledge encryption and end-to-end encryption address the complete lifecycle.
Creation
- A password is generated on your device.
- Zero-knowledge ensures your master password never transmits to the device in plain form.
Storage
- AES-128 encryption protects vaults at rest.
- Client-side encryption ensures only encrypted data is transmitted to servers.
Sharing
- Teams can share credentials safely with All Pass Hub.
- End-to-end encryption ensures no one intercepts credentials in transit.
Retrieval
- Dual protection with login password and master key confirms authenticity.
- Vault data is decrypted only locally on the user’s device.
Rotation or Deletion
- Outdated credentials can be replaced or erased without exposure.
- Zero-knowledge ensures no traceable, readable copy exists on servers.
By covering the entire lifecycle, All Pass Hub eliminates weak points that attackers often exploit, offering ongoing protection instead of partial safeguards.
Smart Summary: From creation to deletion, zero-knowledge and end-to-end encryption secure every stage of a password’s life. It ensures resilience against both interception during transit and unauthorized access at rest.
Read More:- Looking For A Secure Password Manager? Here’s How All Pass Hub Protects You
Balancing Security And Usability In Real Life
Security without usability often gives rise to frustration, which usually leads to unsafe shortcuts. Many password managers fail not because their encryption is weak but because they make everyday use complicated. The challenge is to develop a system that combines top-notch protection with a practical user experience.
To understand how this harmony works, let’s look at common pain points and how All Pass Hub addresses them.
Recovery Concerns
A common misconception is that zero-knowledge makes recovery impossible.
- Reality: All Pass Hub guides users through secure account recovery methods without exposing vault data.
Device Synchronization
Users want access on multiple devices without risking their passwords.
- Solution: All Pass Hub offers unlimited device login and uses end-to-end encryption to synchronize vaults without revealing contents.
Onboarding New Users
Team expansion can create risks if the transfer of login details is not monitored.
- Truth: With controlled unlimited credential sharing, All Pass Hub ensures new members obtain authorization securely.
Everyday Usability
Features such as search by tags, pinning favorite login details, and unlimited team access simplify workflows.
These tools make advanced security feel natural rather than a hindrance.
➡️The result is a synergy where security measures operate in the background while usability remains smooth and intuitive.
What You Should Know: All Pass Hub combines zero-knowledge and end-to-end encryption with practical usability to resolve friction points such as recovery, synchronization, and team onboarding. It encourages safe adoption in daily life.
Benefits Of Zero-Knowledge Password Managers For Businesses And Enterprises
Security technology is valuable only if it delivers tangible improvements. Zero-knowledge password managers supported by end-to-end encryption transform how individuals, teams, and enterprises approach password protection.
To simplify this, let’s walk you through a before-and-after scenario followed by the specific benefits All Pass Hub provides.
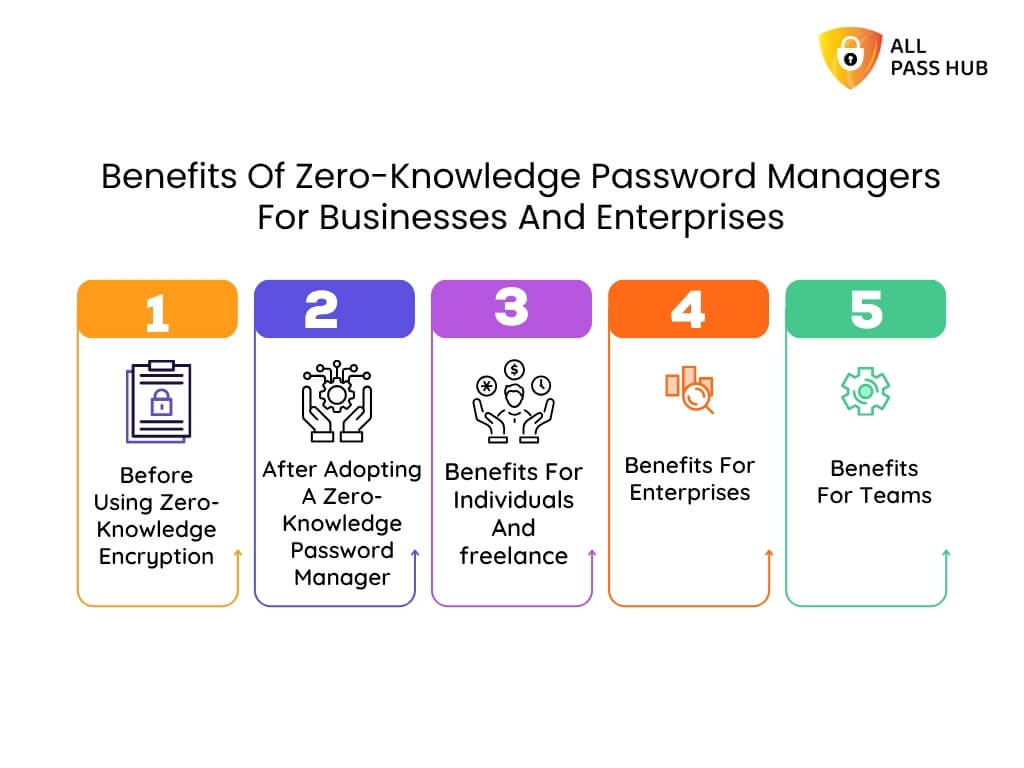
Before Using Zero-Knowledge Encryption
- Teams depend on spreadsheets or shared documents.
- Administrators hold centralized control, creating insider risks.
- Password recovery often means provider access to vault data.
- Compliance reviews are time-consuming and filled with gaps.
After Adopting A Zero-Knowledge Password Manager
- All vaults are encrypted on the client side, making decryption by the provider impossible.
- Teams share credentials peacefully without creating traceable copies.
- Recovery methods remain user-controlled, preserving privacy.
- Compliance audits become more manageable because every vault action leaves a clear log.
Benefits For Individuals
- Safe password storage with zero-knowledge architecture.
- Hassle-free login without exposing private credentials.
➡️Example: A freelance designer can store all client account credentials in All Pass Hub without worrying about someone else accessing them, even if servers are compromised.
👉Note: Individuals can begin with All Pass Hub with a free forever plan.
Benefits For Enterprises
- Compliance-ready solutions aligned with GDPR, CCPA, and PCI DSS.
- Military-grade AES-128 encryption for vaults.
- Enterprise zero-knowledge password solutions that reduce breach risk.
➡️Example: A healthcare company can store patient portal credentials in All Pass Hub while proving compliance during HIPAA audits without exposing sensitive information to employees or vendors.
👉Note: Enterprises can start with All Pass Hub on the premium plan of $0.99/month and $6.99/year. They can also request us for a customized pricing plan for high-end needs.
Benefits For Teams
- Unlimited members can collaborate without expanding vulnerabilities.
- Controlled governance ensures login passkeys remain private even as teams expand.
➡️Example: A remote marketing team can share social media login credentials securely in All Pass Hub, with access controls ensuring only authorized members can use them.
👉Note: Teams can start with All Pass Hub with a free plan or $0.99/month and $6.99/year plan. No credit card required.
This transformation explains why enterprises and startups alike adopt All Pass Hub, not just as a tool but as a trusted safeguard for daily operations.
Quick Recap: Zero-knowledge password managers such as All Pass Hub redefine password management by eliminating insider risks and easing compliance. It provides individuals, teams, and enterprises with a more private and resilient way to protect data.
Read More:- How All Pass Hub Helps High-Performance Teams Manage Credentials Smartly
All Pass Hub In Action: Real-World Use Cases And Outcomes
Knowing the features of zero-knowledge encryption and end-to-end encryption is one thing, but witnessing them in practice reveals their actual value. Organizations of every size face distinct challenges with password management, and All Pass Hub provides tailored solutions.
Let’s explore real-world examples that show how this technology delivers measurable outcomes.
Remote Teams Sharing Credentials Peacefully
- Distributed teams often juggle multiple accounts across time zones.
- All Pass Hub allows seamless password sharing without creating trackable copies.
➡️Example: A global software development team shares cloud server logins securely while maintaining thorough audit trails of every action.
Startups Scaling with Enterprise-Grade Password Management
- Rapid growth can expose startups to breaches if password storage is inconsistent.
- All Pass Hub offers unlimited user access with zero-knowledge encryption.
➡️Example: A fast-growing fintech startup adds new hires weekly while maintaining strict access controls, thereby preventing insider leaks.
Enterprises Reducing Breaches And Costs
- Large organizations require compliance-ready password managers.
- All Pass Hub integrates a zero-knowledge architecture and detailed audit logs for reporting.
➡️Example: An enterprise IT department cut support costs by automating password resets and reducing security incidents through encrypted credential sharing.
These cases demonstrate how All Pass Hub adapts to real-world needs, from small creative teams to regulated enterprises. It ensures privacy and accountability.
The Bottom Line: Whether for remote teams, startups, or enterprises, All Pass Hub applies zero-knowledge and end-to-end encryption. It reduces breach risks, regulates costs, and delivers secure password sharing at scale.
Common Threats And How Zero-Knowledge Stops Them
Cybersecurity threats are evolving rapidly, and attackers constantly seek weak points in password storage and sharing. Traditional methods often leave gaps that can be exploited. It is where zero-knowledge encryption and end-to-end encryption prove vital.
To understand their value, let’s examine the most common risks and how All Pass Hub negates them.
Insider Threats To Stored Credentials
- Threat: Employees or administrators sometimes misuse access privileges.
- Solution: With a zero-knowledge architecture, not even All Pass Hub staff can peep into your vault data.
External Threats Targeting Password Security
- Threat: Hackers attempt to intercept credentials during transmission.
- Solution: End-to-end encryption ensures data is transmitted from your device encrypted and is decrypted only on your side.
Data Breach Risk Prevention
- Threat: Centralized storage often becomes a single point of failure.
- Solution: Client-side encryption means vaults are unreadable even if servers are accessed.
AI-Driven And Large-Scale Attacks
- Threat: Credential stuffing, phishing, and automated attacks are on the rise.
- Solution: Multi-factor authentication and detailed audit logs in All Pass Hub add extra layers of defense.
Supply Chain Attacks
- Threat: Compromised vendors can introduce backdoors.
- Solution: Zero-knowledge and encrypted credential sharing prevent attackers from obtaining valuable data, even if a third party is infiltrated.
These combined armors make All Pass Hub a highly preferred solution that protects passwords from both predictable risks and emerging threats.
Essential Insight: Zero-knowledge and end-to-end encryption work in harmony to prevent insider misuse, block external obstructions, and withstand modern threats like AI-driven credential stuffing and supply chain infiltration.
Misconceptions And Myths About Zero-Knowledge Debunked
Zero-knowledge encryption is often misperceived, which deters many users and businesses from adopting it confidently. Fallacies create hesitation, but once clarified, they reveal why this architecture is among the highly trusted approaches to password security.
Let’s address some of the most typical myths to separate fact from fiction.
Myth 1: Zero-Knowledge Encryption Can Be Hacked Easily
- In reality, brute-force attempts against PBKDF2-SHA256 with hundreds of thousands of iterations are computationally absurd.
- Vaults are protected by AES-128 encryption, making them unreadable even if servers are compromised.
Myth 2: Recovery Is Impossible With Zero-Knowledge
- Many assume that if providers cannot see vaults, users lose all recovery options.
- All Pass Hub offers safe recovery methods that never expose private data while still enabling account restoration.
Myth 3: End-To-End Encryption Is The Same As Zero-Knowledge
- End-to-end encryption protects data during transmission.
- Zero-knowledge encryption ensures even the provider cannot access data at rest.
➡️They serve distinct purposes and become most potent when used in synergy.
Myth 4: Losing The Master Password Means Permanent Lockout
While the master password is integral, All Pass Hub supports additional layers such as multi-factor authentication and secure hints that help without compromising privacy.
By clearing up these misbeliefs, it becomes apparent that zero-knowledge architecture does not create obstacles. In fact, it is a safer and more trustworthy way to manage passwords.
Must-Know Insight: Misconceptions about zero-knowledge often exaggerate its limitations. However, in practice, it combines with end-to-end encryption to deliver privacy, usability, and reliable recovery methods without exposing sensitive data.
Password Manager Security Comparison And Market Outlook
Selecting a password manager often comes down to evaluating how well each one protects sensitive data. With many providers claiming impenetrable storage, it is necessary to understand which features genuinely set solutions apart.
Let’s compare core security practices to bring clarity and explore the market outlook for zero-knowledge password managers.
| Feature | Basic Password Managers | End-to-End Only Managers | All Pass Hub (Zero-Knowledge + End-to-End) |
| Encryption in Transit | Standard TLS protection | Encrypted from device to server | TLS 1.2+ with client-side encryption |
| Encryption at Rest | Provider-managed keys used | Vaults are encrypted, but the provider may still access | AES-128 vault encryption is accessible only by the user |
| Provider Access | Providers often retain recovery access | Restricted but still possible in some cases | No provider access, zero-knowledge architecture ensures privacy |
| Recovery Options | Provider resets are available, creating risk | Limited recovery tied to provider systems | User-controlled recovery without exposing vault data |
| Compliance Readiness | Not always audit-ready | Partial compliance features | Comprehensive audit logs, enterprise-grade compliance alignment |
| Scalability | Limited sharing and team use | Sharing is restricted in practice | Unlimited team members, controlled credential sharing |
| Market Position | Entry-level security for individuals | Better than basic but not complete | Among the best zero-knowledge password managers in 2025 |
With the growing emphasis on regulatory compliance and secure digital collaboration, the demand for zero-knowledge password managers is expected to rise. It will make them an industry standard rather than an optional feature.
The Crux: While some managers stop at basic encryption, All Pass Hub integrates both. It delivers unmatched privacy and positions itself as one of the best zero-knowledge and end-to-end encryption password managers in 2025 and beyond.
Future Of Password Security And All Pass Hub Innovation
The future of password protection is shifting rapidly as attackers adopt next-level tactics and regulations demand more robust safeguards.
Relying on outdated methods will no longer be sufficient. Businesses and individuals alike need password managers that not only meet today’s standards but also anticipate tomorrow’s threats.
To see where security is headed, let’s explore the innovations shaping the future and how All Pass Hub is leading the way.
Password Manager Future Trends
- Movement toward passwordless logins through passkeys.
- Wider adoption of multi-factor authentication to fortify vault security.
Long-Term Benefits Of Zero-Knowledge Architecture
- Continued emphasis on user-owned data with no backdoors.
- Reduced dependency on provider-controlled recovery processes.
Innovations In 2025 And Beyond
- Post-quantum encryption development to prepare for quantum computing threats.
- Advanced suspicious detection to identify unusual login activity in real-time.
Upcoming Encryption Standards
- Evolving compliance frameworks under GDPR, CCPA, and PCI DSS.
- Higher expectations from enterprises for audit-ready, transparent encryption practices.
➡️All Pass Hub is already working to integrate these innovations. It ensures its zero-knowledge and end-to-end encryption remain future-ready while helping organizations maintain trust, compliance, and resilience.
Final Thought: The future of password security lies in innovations like passkeys, post-quantum encryption, and anomaly detection. All Pass Hub is all set to deliver these advancements without compromising zero-knowledge privacy.
Conclusion
Password protection has never been more critical. With billions of credentials traded in underground markets and attackers adopting AI-driven methods, depending on conventional password encryption methods is risky.
Zero-knowledge encryption and end-to-end encryption together offer the privacy, resilience, and compliance that present-day users and enterprises demand.
Throughout this guide, we explored what makes zero-knowledge architecture secure, how end-to-end encryption guards data in transit, and why their combination delivers unparalleled protection.
We also looked at lifecycle safeguards, practical usability, business benefits, real-world use cases, and the future of password management.
All Pass Hub stands out by embedding zero-knowledge and end-to-end encryption into every element of its platform. From PBKDF2-SHA256 with 600,000 iterations to AES-128 vault protection, TLS 1.2+ transmission security, and user-controlled recovery, it delivers a resilient solution built for individuals, teams, and enterprises.
➡️Now is the time to choose a safer way of managing credentials. With All Pass Hub, your passwords remain exclusively yours. You will get the needed assurance, privacy, and confidence that your digital world is protected today and future-ready.
FAQ
What Is Zero-Knowledge Encryption In Layperson Terms?
Zero-knowledge encryption means only you can decrypt your data. The provider never holds your keys. Even if their systems are breached, your information remains unreadable and inaccessible to anyone but you.
Can Zero-Knowledge Encryption Be Hacked?
Directly hacking zero-knowledge encryption is nearly impossible because vaults leverage unbreakable algorithms such as PBKDF2-SHA256 and AES-128. Attacks typically target weak passwords or human error, not the encryption itself, which is mathematically unrealistic.
Why Use End-To-End Encryption For Passwords?
End-to-end encryption ensures your data is transferred from your device to the destination encrypted. Only you can decrypt it, which eliminates risks from hackers, internet providers, or even the service platform.
Which Password Managers Use Zero-Knowledge Architecture?
Not all password managers provide comprehensive zero-knowledge security. Some use end-to-end encryption but retain retrieval authorization. Solutions like All Pass Hub ensure a complete zero-knowledge architecture. It guarantees that only the user governs decryption.
How Secure Is Zero-Knowledge Architecture Compared To Traditional Encryption?
Zero-knowledge architecture is far more secure because it prevents providers from storing usable recovery passkeys. Traditional encryption often leaves partial access, creating vulnerabilities. Zero-knowledge mitigates this by giving total ownership of vault access to users.
What Happens If I Forget My Master Password In A Zero-Knowledge Password Manager?
If you forget your master password, providers cannot reset it. However, platforms such as All Pass Hub offer secure, privacy-respecting recovery methods, such as additional factors or pre-configured recovery options, without exposing vault contents.
Is Zero-Knowledge Encryption Suitable For Enterprises With Large Teams?
Yes, enterprises benefit significantly. Zero-knowledge encryption combined with end-to-end sharing enables unlimited team members to collaborate securely. Even administrators cannot view vault contents, ensuring privacy while maintaining compliance with stringent security standards.


